Microsoft rushed to take action on Wednesday after Defender Advanced Threat Protection (ATP) users reported getting Cobalt Strike and Mimikatz alerts that turned out to be false positives.
Cobalt Strike is a commercial penetration testing tool. However, it has often been abused by malicious actors for its advanced capabilities, including in Ryuk, Sodinokibi and other ransomware attacks.
Mimikatz is a post-exploitation tool designed for harvesting passwords from compromised systems. It too has been used by many profit-driven and state-sponsored threat groups.
It’s not surprising that some Microsoft Defender ATP users had a small heart attack on Wednesday when they saw multiple high-severity alerts for Cobalt Strike. Others reported seeing Mimikatz alerts. In both cases they turned out to be false positives.
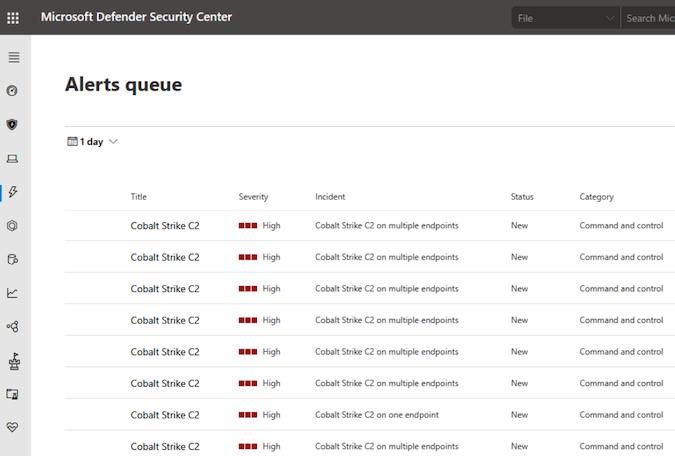
The issue was likely caused by a bad rule pushed to Defender ATP and Microsoft addressed the issue within hours.
“We’ve addressed the issue that led to false positive alerts and corrected notifications some customers may have received,” a Microsoft spokesperson told SecurityWeek.
However, Jon Hencinski, director of SecOps at cybersecurity company Expel and one of the people who monitored the incident, advised organizations not to immediately dismiss Cobalt Strike alerts in Defender ATP and instead follow their triage process as normal.
Related: Microsoft Rushes to Fix Bug That Broke Windows Defender Scans
Related: Microsoft Pulls UEFI-Related Windows Update After Users Report Problems
Related: New VirusTotal Service Aims to Reduce False Positives
Related: Users Unable to Log on to Windows Due to McAfee Update















