Cybersecurity firm Hive Systems has released the results of its latest annual analysis on cracking passwords through brute-force attacks.
Hive has been conducting this study for several years and until now it has targeted passwords hashed with the widely used MD5 algorithm. However, MD5 hashes can in many cases be easily cracked and organizations have increasingly turned to more secure algorithms, particularly Bcrypt.
Bcrypt is not the most secure, but based on data collected by Hive from the Have I Been Pwned breach notification service it has been the most widely used in recent years.
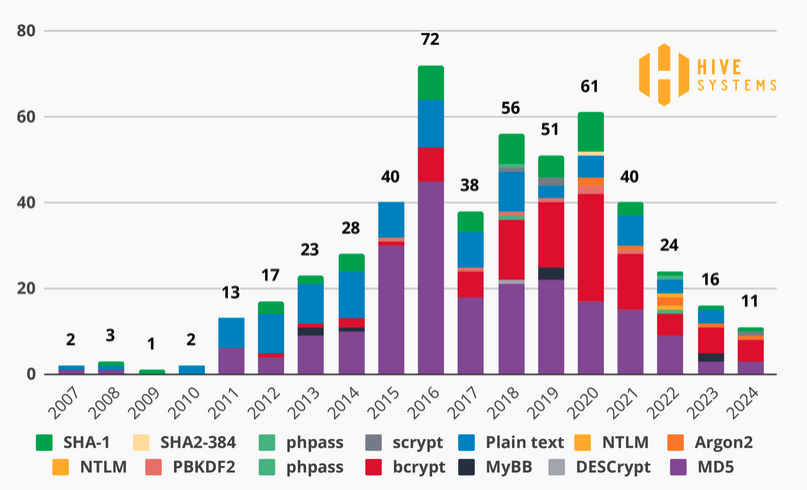
That is why Hive has decided to conduct its testing against Bcrypt password hashes, using a dozen NVIDIA GeForce RTX 4090 GPUs.
The tests showed that any password under seven characters can be cracked within hours. In last year’s tests, weak 11-character passwords were cracked instantly using brute force attacks. With Bcrypt, the same 11-character password now takes 10 hours to crack.
Hive’s analysis showed that strong passwords (containing numbers, uppercase and lowercase letters, and symbols) and fairly strong passwords (containing uppercase and lowercase letters) are difficult to crack if they are more than eight characters long — it takes months or years to crack such passwords if they are protected with Bcrypt.
Hive’s study assumes that the attacker has obtained a hash associated with a randomly generated password and attempts to crack it.
“Non-randomly generated passwords are much easier and faster to crack because humans are fairly predictable. As such, the time frames in these tables serve as a ‘best case’ reference point. Passwords that have not been randomly generated would be cracked significantly faster,” the company explained.
Related: AnyDesk Hacked: Revokes Passwords, Certificates in Response
Related: List Containing Millions of Credentials Distributed on Hacking Forum, but Passwords Old
Related: CISA Urges Manufacturers to Eliminate Default Passwords After Recent ICS Attacks
Related: PoC Tool Exploits Unpatched KeePass Vulnerability to Retrieve Master Passwords














