Systems associated with more than 90,000 unique IP addresses are still infected with a PlugX worm variant that spreads via infected USB drives, bypassing air gaps, cybersecurity firm Sekoia reports.
Over the past six months, Sekoia has been monitoring connections to a sinkholed IP linked to the worm, identifying over 2.5 million IP addresses that connected to it over time.
Of these, between 90,000 and 100,000 unique IPs still send daily requests to the sinkhole, showing that the botnet continues to be active, although its operators no longer have control over it.
However, “anyone with interception capabilities or taking ownership of this server can send arbitrary commands to the infected host to repurpose it for malicious activities,” Sekoia says.
While the PlugX remote access trojan (RAT) has been around since 2008, the self-spreading variant was released in 2020 by a China-linked threat actor tracked as Mustang Panda, likely to exfiltrate data from networks that are not connected to the internet.
The worm adds to the connected flash drive a Windows shortcut file with the drive’s name, and three files for DLL sideloading, namely a legitimate executable, a malicious library, and a binary blob within the drive’s RECYCLER.BIN hidden folder. It also moves the drive’s contents to a new directory.
When the user clicks on the shortcut file, the malware opens a new window displaying the drive’s contents, and then copies itself to the system and creates a new registry key for persistence. Next, it re-executes itself from the system, where it checks every 30 seconds for connected USB drives to infect.
This self-spreading technique, Sekoia notes, has resulted in the botnet expanding uncontrollably across networks, likely pushing its operators to abandon the command-and-control (C&C) server, which could no longer be used for managing thousands of infected hosts.
After identifying a C&C IP no longer in use, Sekoia took ownership of the address and then created the infrastructure needed to manage connection attempts and map their sources.
The security firm was able to identify roughly 2.5 million infected hosts in more than 170 countries worldwide, and observed that the worm was still spreading at an average of 20,000 infections per day.
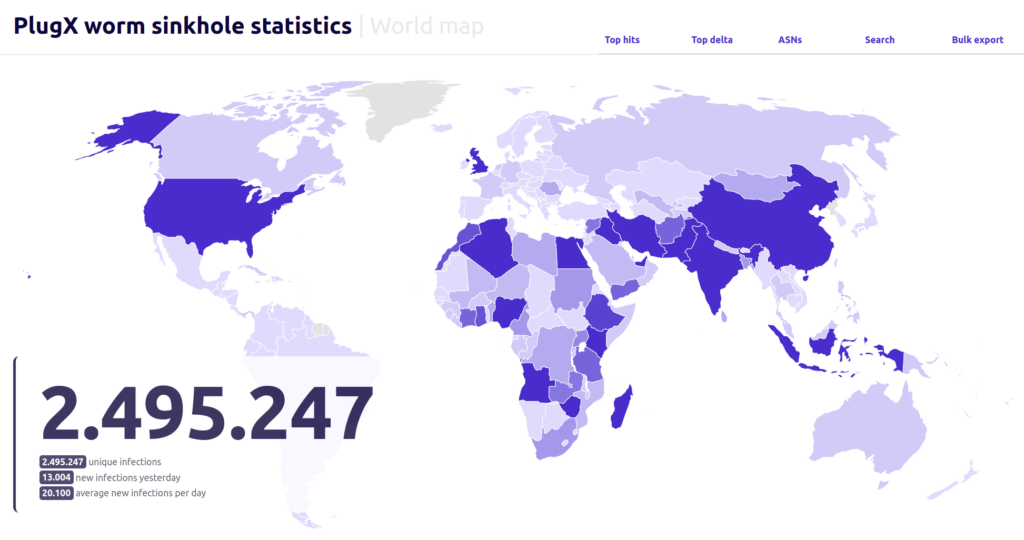
However, the investigation is limited to using IP addresses only, as the worm does not use unique identifiers for its victims. Thus, the total number of infected systems could be different, because some IPs might be used by multiple workstations, while some systems may rely on dynamic IPs.
In early April, however, the security firm detected just over 100,000 unique IPs connecting to the sinkhole. Most of the victims are in countries located in regions of strategic importance to China’s Belt and Road Initiative.
“It is plausible, though not definitively certain as China invests everywhere, that this worm was developed to collect intelligence in various countries about the strategic and security concerns associated with the Belt and Road Initiative, mostly on its maritime and economic aspects,” Sekoia notes.
The company’s analysis of this PlugX variant revealed the existence of a self-delete command and a potential mechanism that could be used to deliver the command to all infected hosts and remove the malware from them.
By delivering a crafted payload, any infected USB drive connected to an infected machine at the time of disinfection could also be cleaned, and the users’ files on those drives fully restored.
However, since the removal payload would not include a persistence mechanism, the worm may not be completely eradicated, as it would remain active on infected flash drives that are not connected to a system during disinfection. Additionally, the malware may also persist on air-gaped systems, as they would not receive the command.
Considering the legal implications of sending the disinfection command, Sekoia decided to contact Computer Emergency Response Teams (CERTs) and law enforcement agencies in the affected countries, providing them with data from the sinkhole and asking them to decide whether the disinfection should be performed.
Related: Chinese APT Hacks 48 Government Organizations
Related: Over 200 Organizations Targeted in Chinese Cyberespionage Campaign
Related: Chinese Cyberspies Use ‘Melofee’ Linux Malware for Stealthy Attacks
















