Threat actors have exploited a Salesforce zero-day vulnerability and abused Meta features in a sophisticated phishing campaign, according to web browsing security company Guardio.
Attackers sent out legitimate-looking emails designed to lure targeted users to a phishing page where they were instructed to hand over their Facebook account information, including their name, account name, email address, phone number, and password.
The emails mentioned the targeted user’s real name, appeared to come from ‘Meta Platforms’, and were sent from an @salesforce.com address.
A button included in the email led users to a legitimate Facebook domain, apps.facebook.com, where they were informed about violating Facebook’s terms of service. When users clicked on a button to resolve the issue, they were taken to a phishing page that instructed them to provide their information.
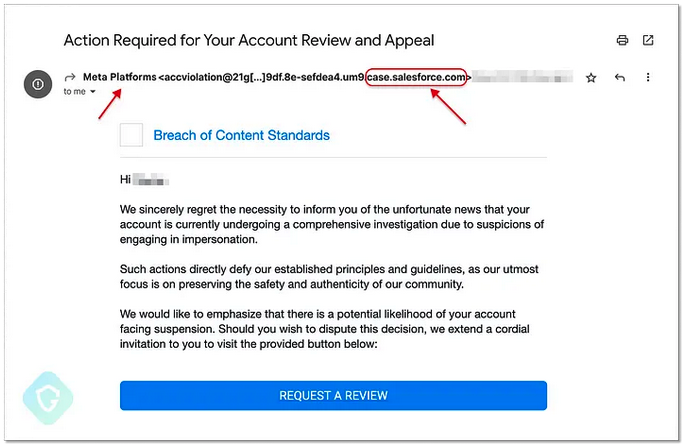
The fact that the email came from an @salesforce.com address and the link it included pointed to facebook.com helped the phishing emails bypass traditional security mechanisms.
Guardio’s analysis revealed that the attackers had targeted the Email Gateway component in the Salesforce CRM, specifically an ‘Email-To-Case’ feature designed to convert customer inbound emails into actionable tickets in Salesforce. By abusing this feature, the attacker managed to receive verification emails that gave them control over a genuine Salesforce email address that they could use to send out the phishing emails.
As for Facebook, the phishing page was hosted on a legacy web games platform offered by Facebook until 2021. While the platform has been discontinued, games developed prior to this date can still receive support and it appears that the attackers gained access to an account associated with such a game. They used that account to host their phishing page.
Guardio notified Salesforce on June 28 and a fix was rolled out to all impacted services and instances within a month, preventing the use of an address from the Salesforce domain to send emails. Salesforce said it had no evidence of impact to customer data.
Meta’s engineering and security teams were also notified and they removed the malicious accounts and game. The company also said it was conducting a root cause analysis to determine why its existing detections and mitigations failed to prevent the abuse.
Related: Salesforce Paid Out $12.2 Million in Bug Bounty Rewards to Date
Related: Companies Still Exposing Sensitive Data via Known Salesforce Misconfiguration
Related: Organizations Warned of Salesforce ‘Ghost Sites’ Exposing Sensitive Information









