A threat actor has control over millions of smartphones distributed worldwide thanks to a piece of malware that has been preinstalled on the devices, Trend Micro warned.
It has been known for several years that smartphones, particularly budget devices, may be shipped with shady firmware that can give companies or other entities access to user data. One of the best known operations involved Triada, an advanced trojan installed on Android devices whose existence came to light in 2016.
Since 2021, Trend Micro has been tracking a different operation that appears to be linked to Triada. The group behind the campaign is tracked by the cybersecurity firm as Lemon Group and the malware preloaded on devices is called Guerrilla.
The campaign has been active since at least 2018, with the threat actor changing the name of its operation from Lemon to Durian Cloud SMS after Trend Micro detailed its operations last year.
In a new report published on Wednesday, Trend Micro said it conducted an analysis of the Guerrilla malware after acquiring a phone and extracting its ROM image for a forensic investigation.
“While we identified a number of businesses that Lemon Group does for big data, marketing, and advertising companies, the main business involves the utilization of big data: analyzing massive amounts of data and the corresponding characteristics of manufacturers’ shipments, different advertising content obtained from different users at different times, and the hardware data with detailed software push,” Trend Micro explained.
“This allows Lemon Group to monitor customers that can be further infected with other apps to build on, such as focusing on only showing advertisements to app users from certain regions,” it added.
An implant planted by Lemon Group loads a downloader that serves as what Trend Micro calls the main plugin, which in turn can fetch and run other plugins.
The secondary plugins can be used to capture SMS messages (including ones containing one-time passwords for popular services such as WhatsApp and Facebook), set up a reverse proxy on infected phones, harvest application data, hijack applications such as WhatsApp to send messages, and deliver ads when launching official apps.
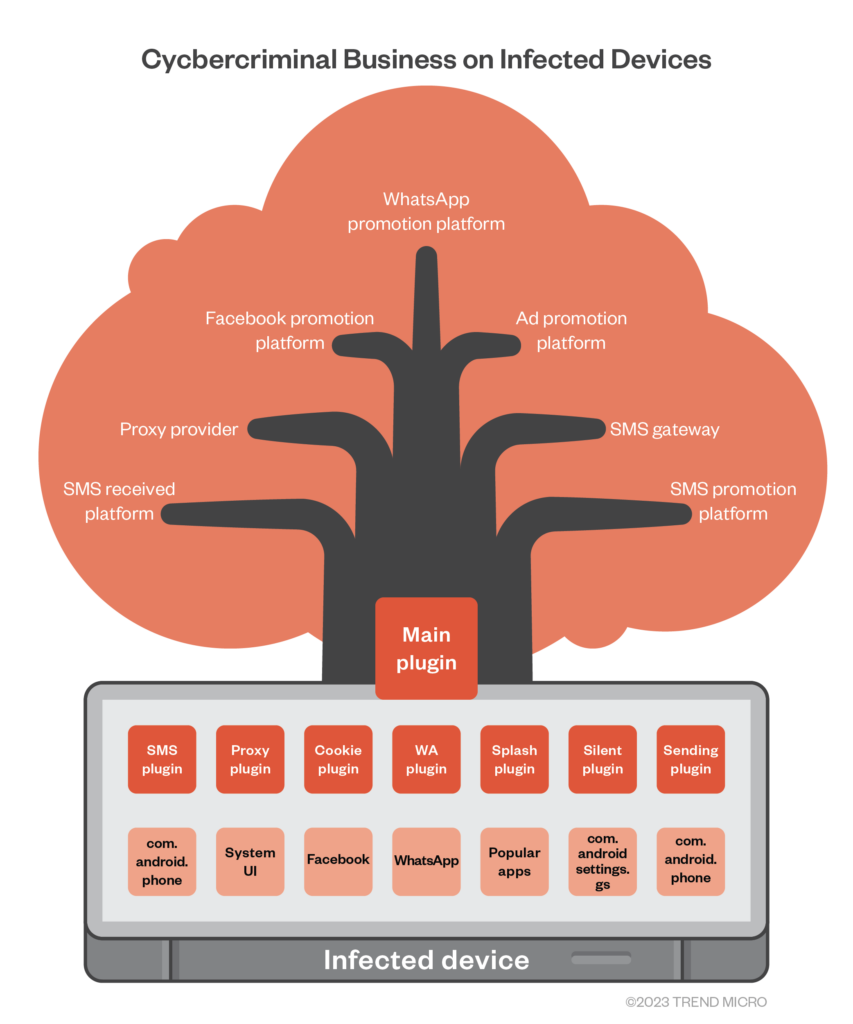
These types of implants are typically placed on devices not by the OEM, but by third-party vendors to which the OEM provides the system image for adding new features. The features they add can include malware such as Guerrilla and the OEM is unaware of its existence.
Trend Micro has monitored requests from devices on which the Lemon and Durian SMS services were active and found more than 490,000 phone numbers across over 180 countries. The top 10 countries are the US, Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, Philippines, and Argentina.
The security firm noted that Lemon Group’s website had advertised that it could reach 8.9 million devices — the page showing these numbers was removed recently — which suggests the actual number of devices preloaded with malware is far greater.
While in this case Trend Micro’s analysis has focused on smartphones, the company has also seen malware from Lemon Group and similar threat actors on smart TVs, Android TV boxes, Android-based smartwatches for kids, and other IoT products.
“Noting our detections for this investigation alone, we were able to identify over 50 brands of mobile devices that have been infected by Guerilla malware, and one brand we’ve identified as a ‘Copycat’ brand of the premiere line of devices from leading mobile device companies,” Trend Micro explained. “A compromise on any significant critical infrastructure with this infection can likely yield a significant profit for Lemon Group in the long run at the expense of legitimate users.”
Related: Triada Trojan Pre-Installed on Low Cost Android Smartphones
Related: Millions of Budget Smartphones With UNISOC Chips Vulnerable to Remote DoS Attacks
Related: Researchers Find Pre-Installed Malware on More Android Phones in U.S.
















