A new attack technique named SMTP Smuggling can allow malicious actors to send out spoofed emails that bypass authentication mechanisms.
SMTP Smuggling was discovered by Timo Longin, a researcher known for DNS attacks, in collaboration with SEC Consult, a cybersecurity consultancy that is part of digital transformation company Eviden.
The attack technique, whose details were disclosed on Monday, targets the Simple Mail Transfer Protocol (SMTP), which is widely used by mail servers to send, receive, and relay emails.
Longin and SEC Consult showed that an attacker can abuse differences in the way outbound and inbound SMTP servers interpret a sequence indicating the end of message data.
“If SMTP servers have a different understanding of where the message data ends, an attacker can potentially break out of the message data,” the researchers explained.
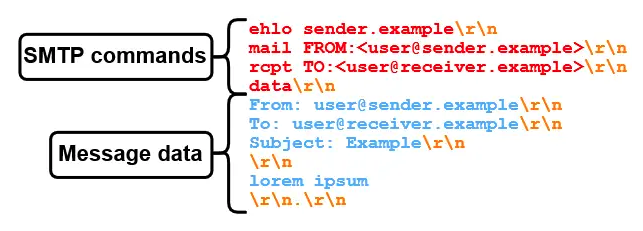
Using SMTP Smuggling, an attacker can send out a spoofed email purporting to come from a trusted domain and bypass the SPF, DKIM and DMARC email authentication mechanisms, which are specifically designed to prevent spoofing and its use in spam and phishing attacks.
An analysis found that the attack technique could allow an attacker to send emails spoofing millions of domains, including ones belonging to high-profile brands such as Microsoft, Amazon, PayPal, eBay, GitHub, Outlook, Office365, Tesla, and Mastercard. The attack was demonstrated by sending spoofed emails apparently coming from the address ‘admin(at)outlook.com’.
However, attacks against these domains are possible — or were possible, because some vendors have applied patches — due to the way a handful of major email service providers set up SMTP servers. The vendors identified by the researchers are GMX (Ionos), Microsoft and Cisco.
The findings were reported to these vendors in late July. GMX fixed the issue after roughly 10 days. Microsoft assigned it a ‘moderate severity’ rating and rolled out a patch sometime in the middle of October.
Cisco, on the other hand, does not view it as a vulnerability and SEC Consult says SMTP Smuggling still works against the default configuration of Cisco Secure Email instances. Changing the configuration of the product prevents SMTP Smuggling attacks.
“We did not analyze all SMTP software out there, hence it might be possible that other vulnerable servers exist as well,” SEC Consult said.
The cybersecurity firm pointed out that while SMTP Smuggling can help bypass email authentication mechanisms, spam filters may still catch the spoofed emails based on their content or other factors.
Related: Google’s RETVec Open Source Text Vectorizer Bolsters Malicious Email Detection
Related: Google Will Start Deleting ‘Inactive’ Accounts in December. Here’s What You Need to Know
Related: Zimbra Zero-Day Exploited to Hack Government Emails










