Menlo Security has introduced two anti-phishing solutions that tackle the problem from within the browser; that is, by analyzing what the user sees on a landing page rather than just analyzing the content of an email.
Phishing has been a problem for decades. Far from being solved, it is a bigger problem today than ever. The reason is that phishers have become adept at evading traditional detection systems. “The threat actors have shifted the way that they get to their victims,” says Mark Guntrip, senior director of cybersecurity strategy at Menlo. They have become increasingly evasive and increasingly successful. “So, we’ve put in place something that does things a little differently to the more traditional and commonly deployed security.”
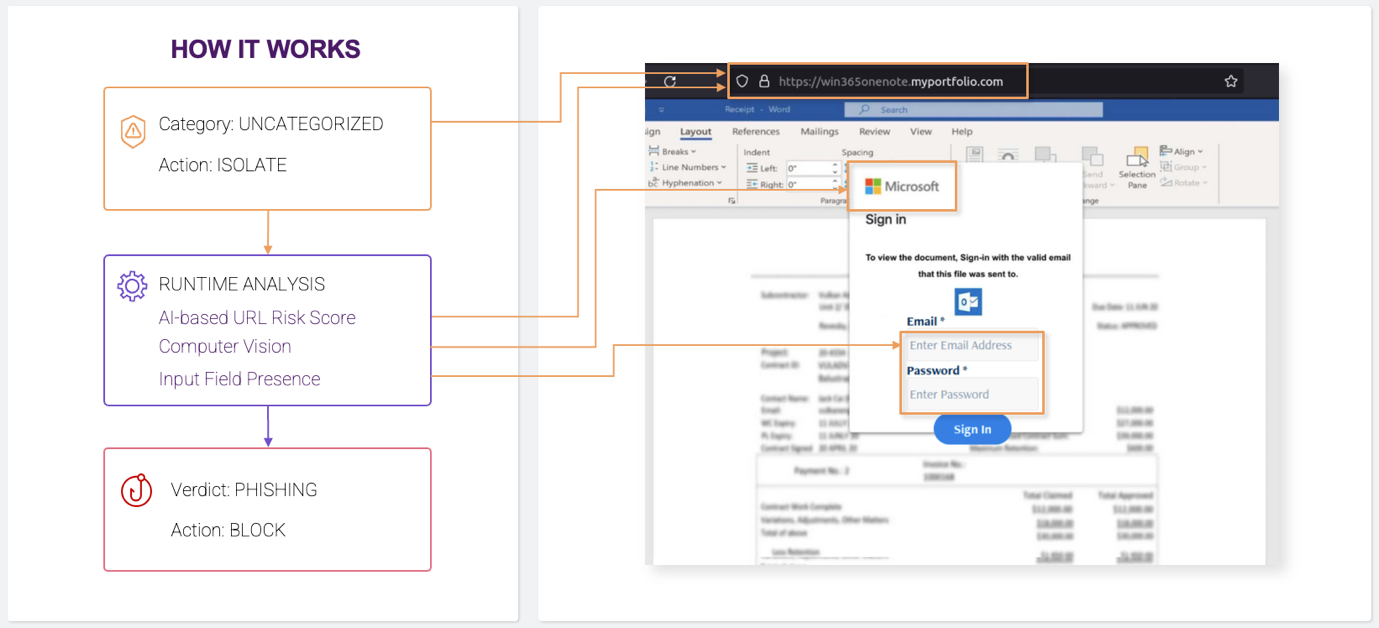
This is performed by new solutions, HEAT Shield and HEAT Visibility. Rather than concentrating on monitoring communications to detect phishing, HEAT looks at the threats as presented to the user on the attacker’s phishing page. The purpose is to recognize the threat at the point of presentation to the user and block the threat at that point. This approach means that any new phishing email that gets through to the user, and is clicked by the user, is still prevented from doing harm.
The linked-page examination is performed by an AI-enhanced analysis of the landing page to assess its legitimacy. “What’s on the website, what logo is being shown? Does the logo look correct for the brand that it represents? What URL is the page coming from, and does it look to be legitimately associated with the brand? What is the page trying to do — Is it trying to download something? Is it a form, and does that form look right or not?” explains Guntrip.
Based on all the information gathered, the solution creates an instant risk score and, if necessary, enforces a dynamic policy change. “Rather than allowing this page, I’m going to put it into isolation.” he continued; “or if I’m sufficiently suspicious, I’m just going to block it dynamically. The whole point is these phishing attacks are now very quick — they come, and they go before human intervention can determine if they are malicious and block them. It’s that zero hour phishing window that we’re trying to play into with a new level of protection.”
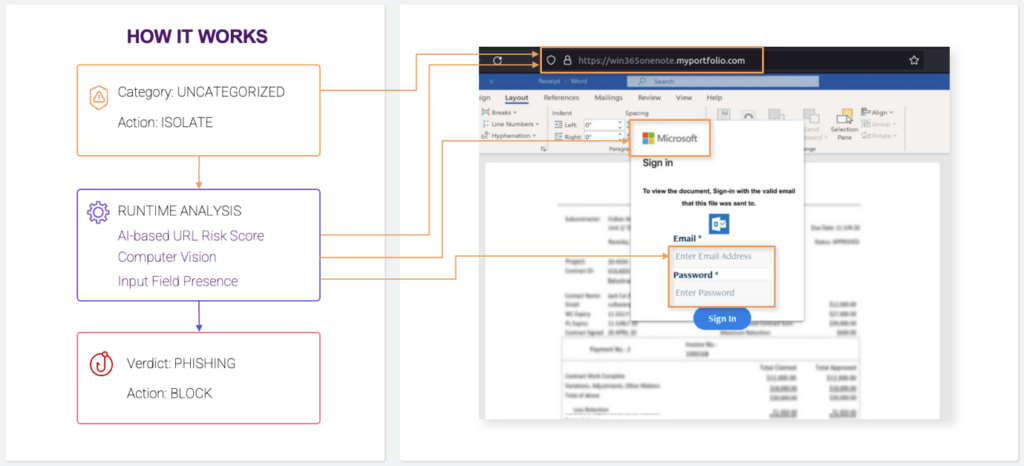
HEAT Shield generates the information that triggers Menlo’s Isolation Platform to perform a dynamic block between the user and the phisher’s website. If a phishing email gets through all other defenses, lands in an inbox and is triggered by the user, Shield can still prevent a malicious site stealing the user’s credentials. The focus is from within the browser — seeing and acting on what the user sees rather than listening to evasive and misleading emails from the phisher.
There is no operational delay to the user. If Shield determines there is no risk, the user continues as if nothing has happened. If the risk score is high enough to trigger a block, this happens within milliseconds – a ‘page blocked’ banner appears immediately.
HEAT Visibility builds data on who is attacking the company, and what evasive tactics are getting through other defenses. “You can see that on a dashboard,” said Guntrip. “You can dive into it to see what’s happening, what techniques the attackers are using. So, it’s really about understanding the phishing threat landscape as it’s impacting the person or the organization.”
HEAT Visibility will be rolled into all existing Menlo subscriptions. HEAT Shield (which includes Visibility) is a separate subscription service if the customer has no other Menlo services. Menlo provides several product bundles, and if a customer already subscribes to one of the larger bundles, Shield and Visibility will both be added at no extra cost.
Mountain View, California-based Menlo Security was founded in 2012 by Amir Ben-Efraim (CEO) and Poornima DeBolle (CPO). It has raised a total of $250.8 million in five funding rounds including: Series A ($10.5 million), Series B ($25 million), Series C ($40 million), Series D ($75 million) and Series E ($100 million).
Related: Threat Actor Abuses SuperMailer for Large-scale Phishing Campaign
Related: New ‘Greatness’ Phishing-as-a-Service Targets Microsoft 365 Accounts
Related: UK Gov Warns of Phishing Attacks Launched by Iranian, Russian Cyberspies
Related: Zendesk Hacked After Employees Fall for Phishing Attack