A researcher has launched Malvuln, a project that catalogues vulnerabilities discovered in malware and provides information on how those vulnerabilities can be exploited.
Malvuln is the creation of security researcher John Page (aka hyp3rlinx), who told SecurityWeek that he came up with the idea when he got bored during a COVID-19 lockdown.
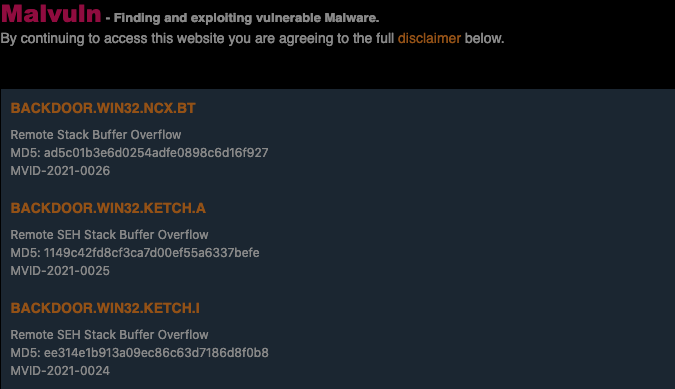
The Malvuln website currently has 26 entries describing remotely exploitable buffer overflow vulnerabilities and privilege escalation flaws related to insecure permissions. The list of targeted malware includes backdoors and trojans, as well as one email worm (Zhelatin). A vast majority of the buffer overflow bugs can be exploited for remote code execution, the expert said.
Each entry contains the name of the malware, its associated hash, the type of vulnerability, a brief description of the flaw, dropped files, a memory dump, and proof-of-concept (PoC) exploit code.
The researcher said he found all the vulnerabilities currently in the Malvuln database himself, but he suggested on Twitter that at some point — depending on where the project goes — he could also start accepting third-party contributions.
Page told SecurityWeek that the information hosted on Malvuln could turn out to be useful to incident response teams to “eradicate a malware without touching the machine if it’s a remote exploit.” He added that it “may eventually pit a malware vs malware situation.”
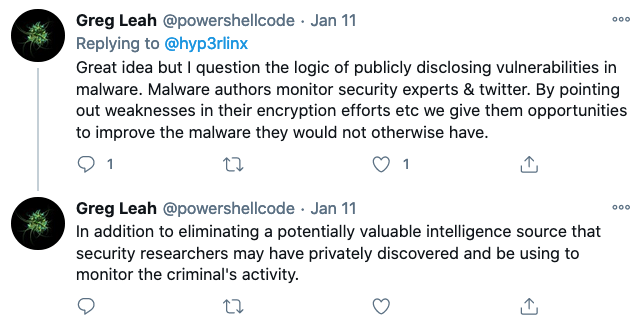
He hopes that the project will be useful to the infosec community, but others caution that it could also help bad actors. Greg Leah, director of threat intelligence at attribution intelligence and response firm HYAS, says the information could also be useful to malware developers and it could hamper ongoing research into malicious activity.
Related: Community Project Crushes 100,000 Malware Sites in 10 Months
Related: University Project Tracks Ransomware Attacks on Critical Infrastructure
Related: Free Microsoft Service Looks at OS Memory Snapshots to Find Malware














