Microsoft on Monday unveiled Project Freta, a free service that allows users to find rootkits and other sophisticated malware in operating system memory snapshots.
Freta is the name of the street in Warsaw, Poland, where renowned scientist Marie Curie was born. The project’s name is related to Marie Curie inventing a mobile x-ray device that could be taken to a battlefield.
The Project Freta cloud-based service currently only supports Linux systems, but Microsoft plans on adding support for Windows as well.
Project Freta aims to provide an agentless way for organizations to conduct automated forensic analysis on thousands of virtual machines in search of malware — ranging from cryptocurrency miners to rootkits — by looking at a captured image of volatile memory.
The service leverages sensors that are designed to detect malware, but without tipping off the malicious software. According to Microsoft, the technology is built so that malware cannot detect the sensor before installing itself, malware cannot hide where it would not be seen by the sensor, the malware cannot detect operation of the sensor and take action to remove or change itself, and malware cannot modify the sensor to evade detection.
The service looks at processes, global values and addresses, in-memory files, debugged processes, kernel components, networks, ARP tables, open files, open sockets, and Unix sockets.
Project Freta is currently available as a portal where users can upload their operating system images for analysis. The results can be accessed directly on the portal or through REST and Python APIs.
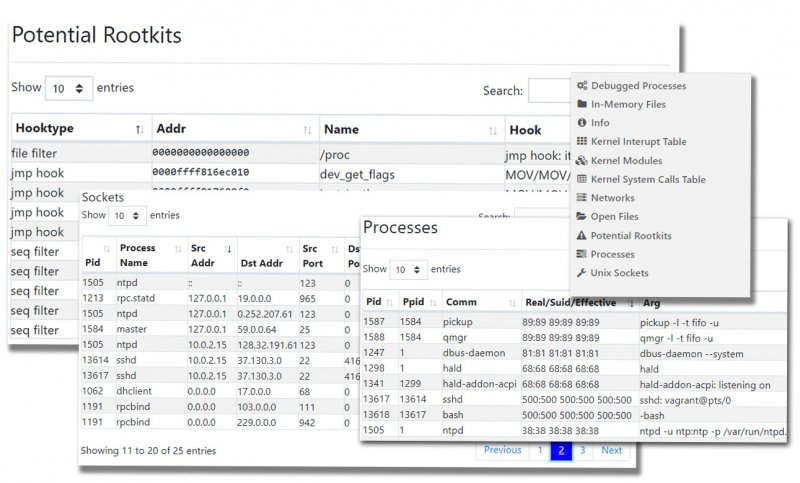
“As a technology demonstration, Project Freta is opening public access to an analysis portal capable of automatically fingerprinting and auditing a memory snapshot of most cloud-based Linux VMs; over 4,000 kernel versions are supported automatically,” Mike Walker, senior director of New Security Ventures at Microsoft, said in a blog post.
In addition to adding Windows support, Microsoft plans on extending analysis capabilities and implementing AI-based decision-making for detecting new threats.
“Project Freta’s second component for achieving trusted sensing is a sensor built for Azure that allows operators to migrate the volatile memory of live virtual machines to an offline analysis environment without disrupting execution,” Walker explained. “Completed in the winter of 2019, this sensor capability is currently only available to Microsoft researchers and is not fielded to any of our commercial clouds—executive briefings and demos are available. This sensor, coupled with the Freta analysis environment, demonstrates a path to cheap, automated memory forensic audits of large enterprises (10,000+ VMs).”
Related: Microsoft Introduces Free Source Code Analyzer















