A team of researchers has demonstrated that hackers can modify 3D medical scans to add or remove evidence of a serious illness, such as cancer.
Experts from the Ben-Gurion University and the Soroka University Medical Center, Beer-Sheva, in Israel have developed proof-of-concept (PoC) malware that uses a machine learning technique known as generative adversarial network (GAN) to quickly alter 3D images generated during a Computer Tomography (CT) scan.
CT scanners are typically managed through a picture archiving and communication system (PACS) that receives scans from the scanner, stores them and then supplies them to radiologists. Data is transmitted and stored using a standard format named DICOM. PACS products are provided by companies such as GE Healthcare, Fujifilm, Philips and RamSoft.
One problem, according to researchers, is that PACS and DICOM servers are often left exposed to the internet. A scan conducted using the Shodan search engine identified nearly 2,700 servers that were connected to the internet. Another issue is that the medical imagery data is in many cases transmitted over the network without being encrypted, which exposes it to man-in-the-middle (MitM) attacks and manipulation.
Malicious actors could directly target PACS that are accessible from the Internet, or they could first gain access to the targeted organization’s network and launch the attack from there. Another attack vector, which the researchers tested during a penetration test conducted in a hospital’s radiology department, involves physically connecting a small MitM device between the CT scanner’s workstation and the PACS network. In these local attacks, the attacker can rely on insiders or they can pose as a technician, the researchers said.
Once the attacker can intercept traffic from the CT scanner, they can use an attack framework, which the researchers have dubbed CT-GAN, to manipulate the images via the GAN technique before they reach the radiologist who interprets the results.
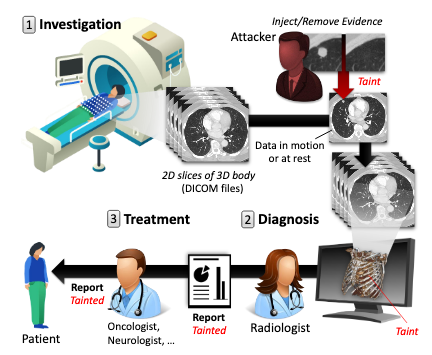
The experts have tested the efficiency of the attack by asking three radiologists to diagnose a mix of 30 authentic CT scans and 70 scans altered using CT-GAN. The malware was used to inject evidence of malign cancer into the scans of healthy patients and remove cancer from the scans of patients who actually had it.
When the radiologists were unaware that the results had been manipulated, they diagnosed 99% of the injected scans as cancer and 94% of the scans from which the cancer was removed as belonging to healthy patients. After they were informed of the attack, the radiologists still misdiagnosed the patients in 60% and 87% of cases, respectively. The researchers said the attack even fooled a state-of-the-art lung cancer screening model in each and every one of the tests.
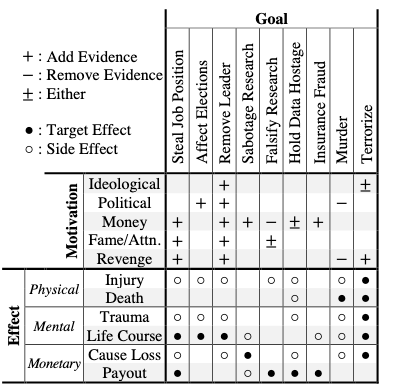
So why would someone want to launch such an attack? The researchers have listed several possible motivations and goals. They believe that modifying someone’s scan and causing a misdiagnosis can be useful for stealing someone’s job, altering elections, sabotaging or falsifying research, earning money by holding data hostage, insurance fraud, and even murder or terrorism.
They pointed out that the method can be used to add or remove evidence of various illnesses, including aneurysms, heart disease, blood clots, infections, arthritis, cartilage problems, torn ligaments, and tumors in the brain, heart or spine.
For example, if an attacker adds evidence of cancer to a political candidate’s CT scan, they can get the targeted individual to withdraw from the race. The same technique could work for getting someone to give up a job or a leadership role. In the worst case scenario, hackers could remove evidence of a serious illness, which could lead to that person dying due to not receiving the proper treatment.
The researchers have published a paper detailing their findings, along with a video showing how an attacker could plant a malicious device inside a healthcare organization.














