
Passwords are currently, and in the foreseeable future, our main method for online authentication. One of passwords most hated features is the complexity requirement that demands the password to have a minimum size, contain mixed-case letters, digits and special characters.
However, a new research paper from Microsoft Research claims that most of the complexity effort is in vain. In this column I’ll explain Microsoft conclusion and then take a look at two, newly presented solutions, to achieve truer password security.
The Online-Offline Password Chasm
Passwords needs to be strong enough to resist a guessing attack, often named a “Brute-force” attack. The brute-force attack comes in two flavors: online and offline. In the online mode of the attack, the attacker must use the same login interface as the user application. In contrast, the offline mode of the attack requires the attacker to steal the password file first, but enables an unconstrained guessing of passwords, free of any application or network related rate limitations.
Microsoft researchers had found out that “an enormous gap exists between the effort needed to withstand online and offline attacks, with probable safety occurring when a password can survive 106(1M) and 1014 (100T) guesses respectively.” As a result, having a not-so-complicated password such as “tincan24” that is “1M strong” (i.e. expected to survive a 1M guess attack) is as good as having a “1T strong” password “7Qr&2M”. Both are strong enough to survive an online attack, but expected to surrender under an offline attack. However, the latter password is much harder to remember.
Furthermore, by breaking down the use cases that necessitates offline guessing protection, the researcher were able to determine that “Offline guessing is a threat when the password file leaks, that fact goes undetected, and the passwords have been properly salted and hashed. In other cases, offline guessing is either unnecessary, not possible, or addressable by resetting system passwords.”
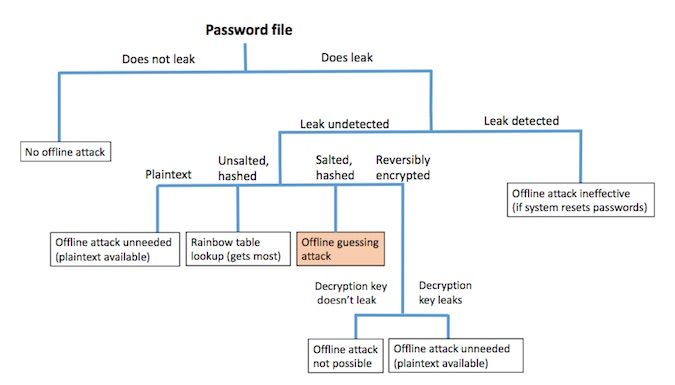
Offline guessing is a threat only when the password file leaks, that fact goes undetected, and the passwords have been properly salted and hashed. Source: Microsoft
Therefore, putting the burden of crossing that eight orders of magnitude wide chasm on the shoulders of the users is both very inefficient and also immoral as it makes the users solves an application problem. By solving the password file leakage problem on the application side, the application can solve the offline brute-force hazard and relax the requirements on the complexity of the users’ passwords.
Solving the Password File Leakage Problem
In order to prevent the password file from leaking to the outside world, it needs to be bounded to the application environment. The common solution, mentioned in Microsoft paper, is to encrypt each password and store the secret key in a Hardware Security Module (HSM). Since the HSM does not provide access to the stored secret key, password decryption can only take place in the application’s environment.
Recently two other innovative solutions to this problem were presented:
1. At Derbycon 2014, Benjamin Donnelly and Tim Tomes presented their “Ball and Chain (BAC) ” construction. BAC provides a method to artificially inflate the passwords file size and spread the password data securely across it, to make the exfiltration of it infeasible. For example, it would take an attacker at least a month to send a 2TB password file over a regular internet connection. Besides taking a long time, the large amounts of data being sent should raise a security flag.
2. Dyadic , a new Israeli start-up company, had revealed its Distributed Security Module. By using the cutting-edge crypto technology of MultiParty Computation (MPC), the DSM splits each password secret across several servers. The attacker needs to breach the security of all involved servers in order to reveal the password. Since the servers can have different access credentials and even operating systems it makes the attacker task much more difficult.
The Take Home Message
Since “passwords are the worst form of authentication except all those other forms that have been tried”, understanding their true pros and cons is highly relevant to the security of our systems. Therefore, defeating offline brute-force attacks should be addressed by the application through any of the aforementioned methods, and not to be handled as an extra burden on the users, via “password complexity”.












