An analysis of 17 espionage frameworks designed to target air-gapped networks shows that all of them leverage USB drives and all target Windows exclusively, ESET reports.
The list was created over the course of 15 years, but the last four of the frameworks emerged last year, proof of an increased interest by threat actors to target isolated systems. Only malware components working together to create an offline, covert communication channel between air-gapped networks and a threat actor were taken into consideration for the study.
Air-gapped networks are meant to protect highly sensitive data, which makes them appealing targets for highly-motivated adversaries, such as nation states, which have the necessary resources to mount attacks against these isolated systems.
In fact, some of these have been attributed with high confidence to nation-state threat actors, such as DarkHotel (the Retro and Ramsay frameworks), Sednit (USBStealer), Tropic Trooper (USBFerry), Equation Group (Fanny), Goblin Panda (USBCulprit), and Mustang Panda (PlugX).
Attribution of tools such as Flame, miniFlame, Gauss, Agent.BTZ, ProjectSauron, Stuxnet, and USBThief hasn’t been as straightforward (Agent.BTZ is believed to be part of Turla’s portfolio), while other frameworks, documented in Vault7 leaks, haven’t been encountered in the wild (Brutal Kangaroo, Emotional Simian, and EZCheese).
Taking a deep dive into these tools, ESET discovered a variety of similarities between them, such as the fact that all are meant to target Windows systems for some form of espionage, and that most of them rely on malicious LNK or autorun files on USB drives for initial compromise or lateral movement.
“Despite the variety of threat actors behind these frameworks, all of them shared a common purpose: espionage. Even Stuxnet, best known for its sabotage capabilities, collected information about Siemens Simatic Step 7 engineering software projects found in compromised machines,” ESET notes.
While Stuxnet has long been said to be the first malware to target air-gapped systems, a sample of Sednit’s USBStealer has been dated all the way back to 2005, suggesting that it was the first of the kind — USBStealer was publicly detailed for the first time in 2014, nine years later.
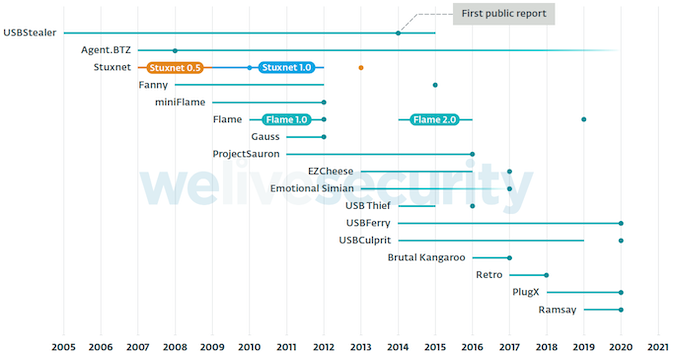
Most air gap-targeting frameworks, ESET also says, became inactive shortly after being publicly disclosed, likely because their operators stopped using them. However, it is also possible that anti-malware solutions on the air-gapped systems were not updated and could no longer detect them.
ESET refers to some of the analyzed frameworks as connected, because they rely on compromised Internet-connected computers to weaponize USB drives to compromise the targeted air-gapped systems. The payload deployed on the air-gapped machine harvests information and places it back on the USB drive. Once the drive is inserted into the compromised connected system, the data is sent to the attacker.
Some of the analyzed frameworks implement a two-way communication protocol, where commands are passed on to the malware deployed onto the air-gapped network.
In other cases, a malicious operator on the ground handles the actions performed by the connected system, such as installing malware onto the USB drive, infecting the air-gapped network, extracting the stolen data from the drive, and sending commands to the air-gapped system.
According to ESET, no evidence of the “use of covert physical transmission mediums, such as acoustic or electromagnetic signals” as part of these frameworks has been found.
The initial infection vector may include spear-phishing emails carrying malicious attachments, the malware’s worm-like capabilities, installation performed by a different malicious component, the use of exploits, and spear-phishing emails exploiting zero-days, among others.
Typically, the malware is installed on the air-gapped system with the help of malicious LNK files that exploit vulnerabilities in older Windows components, such as CVE-2010-2568 and CVE-2017-8464 (and potentially CVE-2015-0096). Over the past 10 years, Microsoft addressed roughly a dozen LNK flaws leading to remote code execution.
The malware may also be deployed using automated execution (by relying on AutoRun/AutoPlay), by tricking an unsuspecting user into executing the malicious code, or by relying on a human actor to deliberately run the malware.
Some of the analyzed frameworks were designed to achieve persistence on the air-gapped systems, and could also receive commands from the attackers, while others were executed in memory, for the collection and exfiltration of data.
The purpose of the air-gapped frameworks is espionage, which includes gathering and exfiltrating system information (computer name, username, domain name, directory/process lists, etc), performing network reconnaissance, looking for specific files to steal, or taking screenshots at specific intervals. For lateral movement, infected USB drives or network-based propagation were used.
Keeping air-gapped networks protected from cyberattacks means detecting and blocking the malicious activities typically associated with malware that targets such systems. Possible mitigations include disabling direct access to emails on connected systems, disabling USB ports on air-gapped systems, sanitizing USB drives that are inserted in air-gapped systems, preventing execution on removable drives, and keeping air-gapped systems updated at all times.
“Despite the use of various techniques to breach the initial air-gapped system, to propagate inside the network or to exfiltrate stolen information, all the frameworks share one common goal: spy on their target. Discovering and analyzing this type of framework poses unique challenges. They sometimes are composed of multiple components that all have to be analyzed together in order to have the complete picture of how the attacks are really being carried out,” ESET concludes.
Related: Bridging the Air Gap: Examining Attack Vectors into Industrial Control Systems















