The Flame platform was believed dead following public exposure in 2012, but recently discovered evidence suggests that it remained alive, albeit very well hidden, security researchers at Alphabet-owned Chronicle reveal.
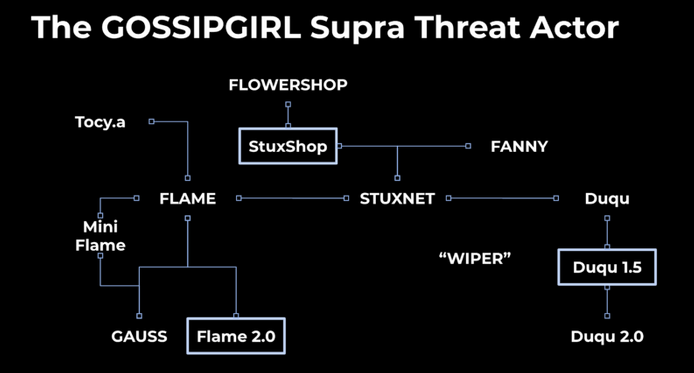
Connected to Stuxnet and Duqu through the activity cluster tracked by Chronicle as GossipGirl Supra Threat Actor (STA), Flame was first detailed in May 2012, following attacks on several countries, mainly Iran and Israel. The Flame backdoor was found to include worm-like capabilities and is said to have been in use since 2009.
The same as Duqu and Stuxnet, Flame has a modular design, providing attackers with the ability to gather system information, beacon to nearby Bluetooth devices, implement network replication, propagate to other machines or removable media, create backdoor accounts, and more.
Following public exposure, the attackers attempted a cleanup by distributing a “suicide” module to remaining infections. This was, as experts described it, “a particularly clunky way of burning down operations as it gave researchers a full list of the components and directories that the operators sought to delete,” but suggested that Flame was gone.
The investigation into GossipGirl, however, led to the discovery of Flame samples that were compiled after 2012, with some builds likely created in February-March 2014, two years after the initial cyberespionage operation was burned down, Chronicle reveals in a report shared with SecurityWeek.
The researchers believe these samples, which were built on the Flame source code and packed new counter-measures against researcher meddling, were used in operations in the 2014-2016 timeframe.
The Flame 2.0 platform employs multiple modules controlled by an orchestrator reliant on an embedded Lua VM. The modules are AES-256-encrypted, with the key passed to the orchestrator upon execution in the form of an argument to the various DLL exports.
The experts were unable to decode the embedded modules, which prevented them from determining the full functionality of the attack toolkit, but said it was likely designed to support lateral movement, create files, and check for anti-virus programs, among others. Overall, however, the Flame 2.0 platform remains largely a mystery.
During their analysis of the GossipGirl STA, Chronicle researchers also discovered a new Stuxnet module suggesting that a fourth team was involved in the malware’s development, and Duqu 1.5, which demonstrated that the threat actor behind the malware remained active after its exposure in 2011.
Related: New Module Suggests Fourth Team Involved in Stuxnet Development
Related: Duqu Remained Active After Operations Were Exposed in 2011













