Trend Micro’s Zero Day Initiative (ZDI) on Wednesday announced the targets, prizes and rules for Pwn2Own Vancouver 2022, scheduled to take place May 18-20 alongside the CanSecWest conference.
This year’s Pwn2Own will be hybrid — participants can attend in person in Vancouver or they can tune in remotely and have their exploits run by ZDI staff. Registration closes on May 12.
Tesla, Zoom, Microsoft and VMware will have representatives at Pwn2Own, with ZDI announcing more than $1 million in cash and prizes for exploits targeting virtualization products, web browsers, enterprise applications, servers, enterprise communications software, and cars.
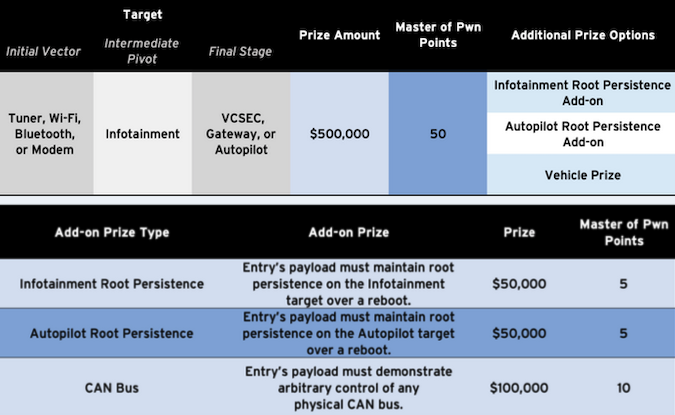
In the case of Tesla, the prizes are largely the same as in the previous year, when no entries were submitted in the automotive category. However, at Pwn2Own 2022, both a Model 3 and a Model S are available as targets. In addition to a top prize of $600,000 for hacking a Tesla, researchers can earn the car itself.
In the virtualization category, the top prize is $300,000, offered for Microsoft Hyper-V exploits. In the web browser category, rewards range between $50,000 and $150,000, which does not include a bonus of up to $75,000 for VM escapes.
In the enterprise app category, researchers can earn up to $50,000 for Adobe Reader exploits and $100,000 for Microsoft Office 365 exploits. Hacking Ubuntu and Windows 11 will be rewarded with up to $40,000.
The Samba interoperability suite has been added to the server category, with rewards of up to $75,000. The highest prize is offered for Windows RDP and Exchange exploits.
Finally, in the enterprise communications category, up to $150,000 is offered for Zoom and Microsoft Teams exploits. At the previous Pwn2Own, two teams did earn $200,000 each for Zoom and Teams exploits.
At last year’s event, which took place in April, participants earned a record-breaking $1.2 million for exploits targeting Safari, Chrome, Edge, Windows 10, Ubuntu, Teams, Zoom, Parallels, and Microsoft Exchange.
In the fall, at Pwn2Own Austin 2021, participants earned a total of more than $1 million for their router, printer, NAS, smartphone, and smart speaker zero-day exploits.
The only event comparable to Pwn2Own in terms of prizes is China’s Tianfu Cup, where participants last year took home a total of $1.9 million.
Related: Printers Hacked for First Time at Pwn2Own
Related: $200,000 Awarded for Zero-Click Zoom Exploit at Pwn2Own














