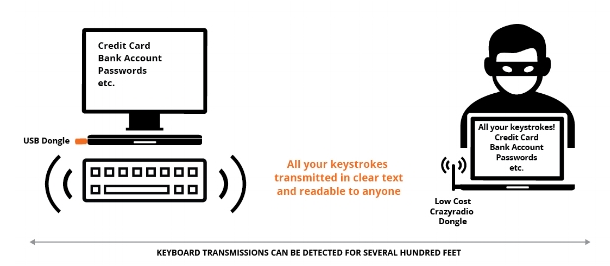
Wireless keyboards from several vendors don’t use encryption when communicating with their USB dongle, allowing remote attackers to intercept keystrokes or send their own commands to the targeted computer.
The attack method, dubbed KeySniffer, was discovered by researchers at IoT security company Bastille. Experts tested non-Bluetooth wireless keyboards from 12 manufacturers and determined that devices from eight of them are vulnerable to KeySniffer attacks.
Bastille said the affected products are inexpensive wireless keyboards from HP, Toshiba, Insignia, Kensington, Radio Shack, Anker, General Electric and EagleTec. It’s possible that products from other companies are impacted as well. Experts determined that higher-end keyboards produced by firms like Lenovo, Dell and Logitech are not affected as they encrypt communications.
KeySniffer attacks are possible because some keyboard manufacturers use unencrypted radio communication protocols. Experts have demonstrated that an attacker using equipment worth less than $100 can launch attacks from distances of up to 250 feet.
Since the affected keyboards send keystrokes in clear text, a remote attacker can use a widely available long-range USB radio dongle, such as Crazyradio PA, to intercept communications. Since the vulnerable devices continuously transmit radio packets – regardless of whether the user is typing or not – it’s easy for an attacker to scan a building or an open space for potential targets.
Researchers have demonstrated that an attacker can easily capture all the victim’s keystrokes and then search the obtained strings for valuable information, such as email addresses, usernames, passwords, and payment card information.
In addition to eavesdropping, an attacker can exploit KeySniffer to inject their own keystrokes, which can allow them to install malware, steal data or conduct other activities on the victim’s device.
Bastille has informed the affected vendors about the vulnerability, but the company believes there is nothing that can be done in most cases since the devices don’t support firmware updates. Kensington informed the security firm that it has released a firmware update to address the issue.
This is not the first time Bastille has found such vulnerabilities. Earlier this year, the company warned that wireless mice and keyboards from several top vendors were vulnerable to so-called MouseJack attacks, where malicious actors send key press packets to a targeted computer through the affected device’s USB dongle in an effort to conduct arbitrary actions. MouseJack is particularly effective against wireless mice because these devices typically don’t use encryption and proper authentication mechanisms.
The MouseJack vulnerability was found to affect more than 80 percent of organizations. Several vendors, including Microsoft, Logitech and Lenovo, released firmware updates to address the weakness, while others provided recommendations on how to mitigate the threat.
Related: Serious Vulnerability Affects Over 120 D-Link Products
Related: Wireless ISP Modems Plagued by Serious Vulnerabilities












