Cloud security firm Sysdig has enhanced the cloud detection and response capabilities of its CNAPP offering with a realtime cloud attack graph. This serves two primary purposes: the ongoing ability to locate and harden potential attack paths; and the ability to detect and remediate an existing attack in realtime.
The full list of enhancements to the existing CNAPP comprises the cloud attack graph, risk prioritization, attack path analysis, a searchable inventory, and complete agentless scanning. The most dramatic is the realtime visual graph.
“If you’re just dealing with misconfigurations or vulnerabilities, this will help you prioritize what to fix,” Knox Anderson, VP of product management at Sysdig, told SecurityWeek. Getting started is quick and easy. With agentless scanning, “You can give us credentials to your cloud account, and within minutes, we’ll start to understand what you have deployed and the misconfigurations that exist. Then, within the first couple of days, you’ll start to understand the potential hotspots that need attention, and you can start driving remediation. After that, we typically see customers deploying agents for deeper visibility to find out more about the activity that’s happening in their environment. But,” he added, “most cloud environments are a mess.”
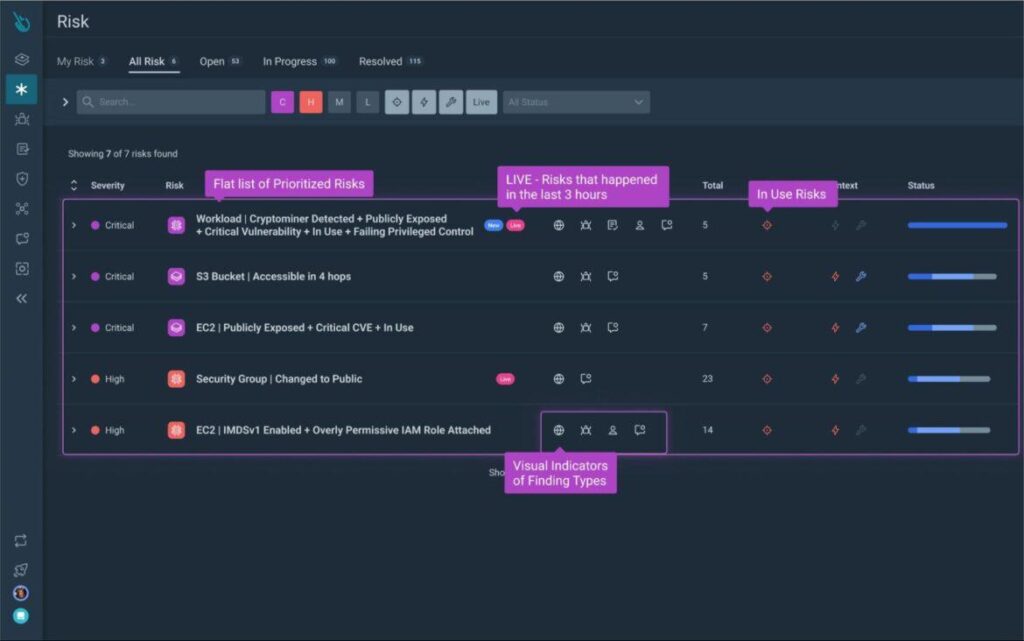
It would take time to fix everything, and in the meantime, unfixed vulnerabilities could be attacked. According to an associated blog, “Cloud attackers are spending less than 10 minutes to execute an attack. Compare this to the median dwell time on-premises of 16 days (Mandiant).” Defenders need to be able to detect and stop a cloud attack in almost realtime.
Detection is already available through the Falco runtime insights built into the CNAPP. The new attack graph can pinpoint a compromise and immediately and visually display actual or potential lateral movement toward specific assets. This visualization comes with recommendations for defensive action — it allows the defender to use the very same qualities of cloud infrastructures that make attacks so rapid, to make defense equally rapid.”
“If you suffer a breach and get alerted in seconds and minutes, you can take that server offline or kill the container or change your permissions instantly,” continued Anderson. “You can take advantage of the speed of changing infrastructure in the cloud that you would normally use for development and provisioning.”
But this all depends on being able to detect, understand the attackers’ lateral movement, and quantify the potential blast radius in realtime.
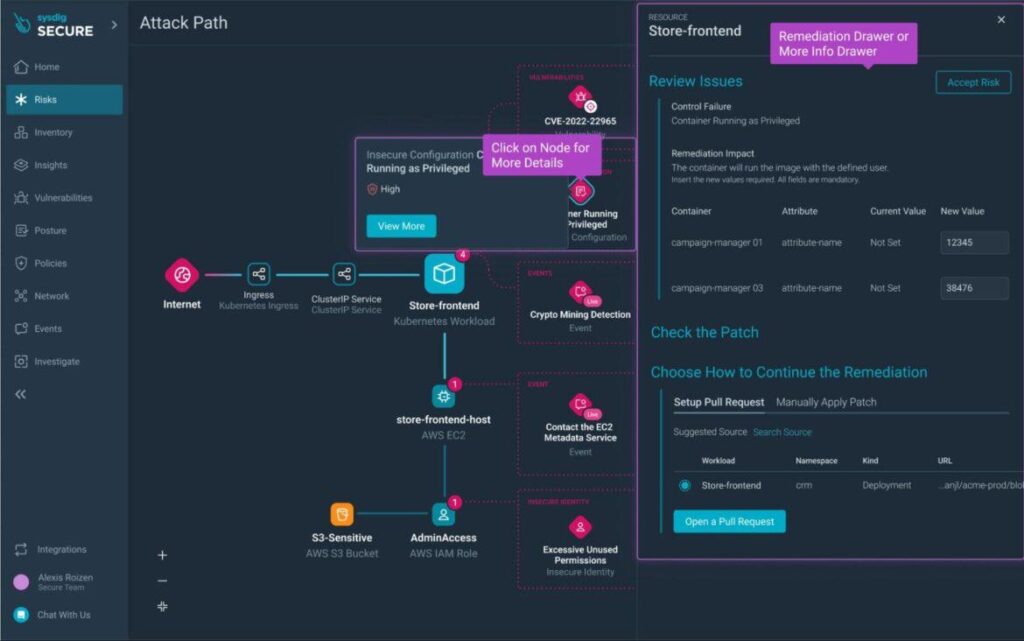
“Security teams need a tool that sees everything, correlates it, and distills it into actionable insights within seconds,” said Anderson. “Context and speed are everything in the cloud, making runtime insights a critical capability for cloud security.”
This is the purpose of Sysdig’s new Cloud Attack Graph: “The Cloud Attack Graph’s real-time insights expedite accurate detection of complex attacks and accelerate incident response,” claims the blog.
Related: Investors Betting Big on Upwind for CNAPP Tech
Related: Sysdig Introduces CNAPP With Realtime CDR
Related: Finding Your Way in Cloud Security
Related: These Are the Top Five Cloud Security Risks, Qualys Says













