According to Gartner, Cloud Native Application Protection Platforms (CNAPPs) “are a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production.” It is an emerging and rapidly growing approach to cloud security.
By 2025, Gartner expects 75% of new cloud security posture management purchases will be part of an integrated CNAPP offering; but few current CNAPPs offer the required breadth and depth of functionality with integration between all components across development and operations. One of the capabilities that Gartner recommends for future CNAPPs is the inclusion of CDR.
It is against this background that Sysdig is launching what it claims to be the first CNAPP with end-to-end detection and response, consolidating CNAPP and CDR. Agentless CDR is provided with the integration of Falco threat detection — an open source tool originally developed by Sysdig, but now under the stewardship of the Cloud Native Computing Foundation — for processing cloud logs to detect threats across cloud, identity, and the software supply chain (and other sources).
It can be used to detect threats against Okta by stitching Okta events with realtime cloud and container activity. It extends threat detection into the GitHub software supply chain by providing alerts on critical events such as a secret being pushed into a repository. And it improves drift control by dynamically blocking executables that were not in the original container.
“With this announcement,” comments Loris Degioanni, CTO and founder at Sysdig (and original developer of both Falco and Wireshark), “we are adding the ability to detect and respond to threats in the cloud to our CNAPP platform. We do this by leveraging Falco in either an agent or agentless configuration to collect the signals coming from cloud apps, cloud infrastructure, and additional tools, and putting everything together into a single runtime detection.”
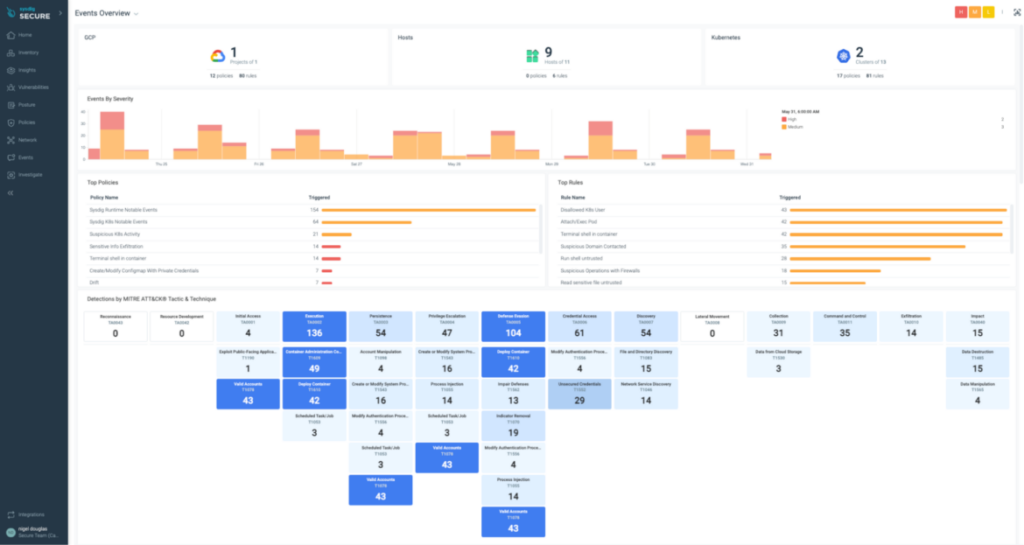
Response is provided through live mapping where defenders can see their live infrastructure and workloads, as well as the relationships between them. Context is provided by presenting the attack journey from user to process, including process lineage, container and host information, malicious user details, and impact. At the same time, curated dashboards provide a centralized view of critical security issues — and dynamic mapping against the MITRE framework for cloud-native environments explains exactly what is happening at any given moment.
Karl Maire, Platform Tech Team Lead at Fuel50, comments, “In the cloud, everything happens fast. Time is of the essence when stopping attacks. Breaches can be very costly. [This CNAPP] enables us to quickly detect and respond to cloud attacks at cloud speed by knowing what is happening, the exact container or location in the cloud, and what is causing it, versus hours to detect and understand what needs to be done”.
Essentially, the primary advance in Sysdig’s new CNAPP is the ability for realtime detection and response. “We’re based on this Falco technology, which is like a runtime detection tool,” explains Degioanni. “We apply this to different types of logs, and we embed everything in our platform. The beauty is that you’re able to react in a matter of seconds. This is a necessity for cloud protection tools, because without that, things change so rapidly that by the time you detect it, the damage is already done.”
Related: Sysdig Raises $350 Million at $2.5 Billion Valuation
Related: DevSecOps Company Sysdig Raises $188 Million at $1.19 Billion Valuation













