Navigating cloud security today can be challenging to understand. Many security professionals ask themselves, what is the best way to secure the cloud? With about 400 vendors at Black Hat USA 2023 and 500 vendors at RSA Conference this year, the choices can be overwhelming. This seemingly simple question has since evolved into a complex and bespoke answer, one which often takes months of work to identify all the key architecture and design choices to make the right decision for your organization. When you finally decide the key areas that need security attention and resources, take a little bit of time to evaluate your risk level, deployment strategy and coverage areas.
Keeping up with changing times
Let’s admit that cloud security is not static. Cloud has evolved a lot over the last 10 years, and it will look very different 10 years into the future. In the early 2000s, it started at the network level, driven in large part by the advances in SD-WAN and virtual networking appliances. We saw firewalls, network intrusion detection, and other isolation methodologies get adopted within the cloud to ensure proper segmentation of data and isolation of resources.
Since the early days, with more and more cloud services being offered every month, security vendors were looking to expand their footprint to ensure proper coverage and respond to market demand. One great example of this is how virtual infrastructure, things like virtual servers or databases, natively supported most of their settings being abstracted into text files that could be used for automated provisioning of cloud resources. These text files could be then analyzed for misconfigurations or security issues before they were deployed into the cloud. Another example is how big names change with the times. Palo Alto and Fortinet started with enterprise grade firewalls, they now offer products across many cloud security areas. CrowdStrike and SentinelOne started with enterprise endpoint protection and have since expanded into cloud workload protection.
What we see in cloud as well as the cloud security market is three-fold. First is the rapid creation of new technologies to keep up with the changing cloud landscape. Second, the overlap with existing technologies and corporate expansion. Third, we see the intricate maze of marketing terms, which trying to help educate and group new technologies together. One of the major issues is that all these changes create confusion in the marketplace, often requiring numerous demonstrations, explanations, and checklists of features.
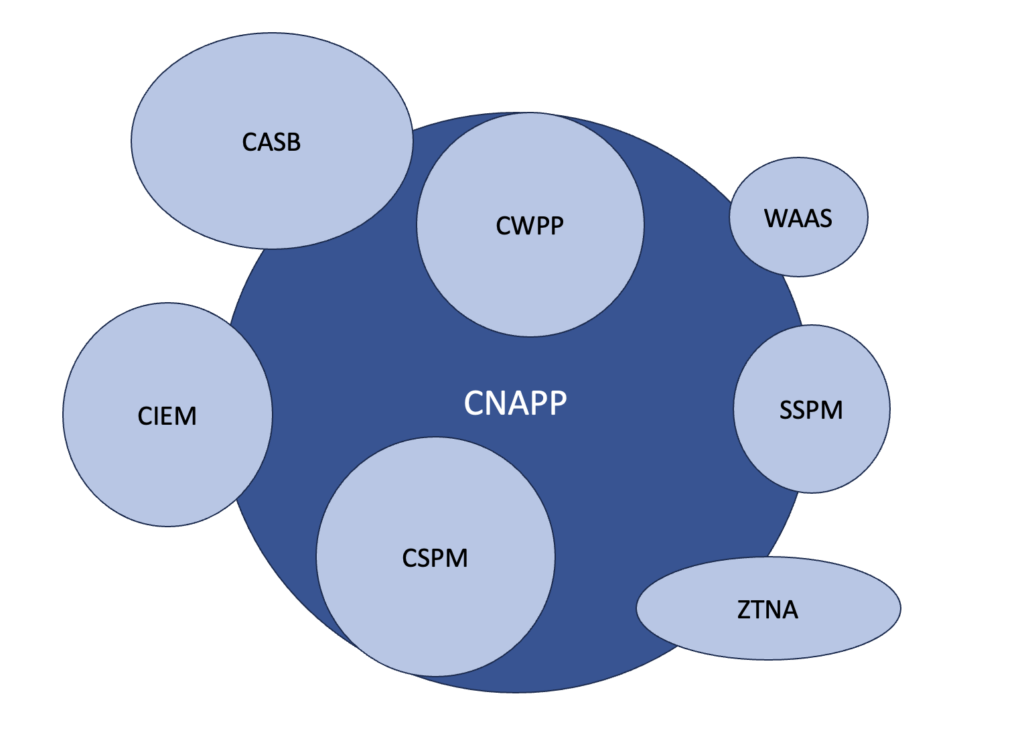
Cloud Compass
I propose an experiment, find two security leaders and ask what CNAPP is? Depending on tenure and security background, the answer will vary greatly. One of the issues I have with the term “cloud security” is that cloud security and enterprise security are blending more than ever today. Many enterprises offer hybrid deployments, often trying to take advantage of scalability in the cloud with cost savings in data centers. When we think of cloud, we need to move away from thinking the big cloud vendors, and just think of the next step in enterprise security.
If you need help, my suggestion is to boil it down to four key areas, and what protections you have in place to mitigate your risk in those areas. This will help you will wipe away your doubt and understand the needs of your organization first before finding a solution that fits.
Workloads: This is your running, high-value applications that process data. Think about what data is exposed and how they communicate with each other and externally.
Identity: This is the who or what touches every point of your infrastructure, things like developers or service account. Think about how these are managed, verified, and have permissions reduced.
Posture: This is the many configurations, settings, networking, security groups and all of the millions of other pieces that exist within one or more architectures. Think about how these settings are checked and verified continually.
Enterprise: This is the pipeline, code, deployment and integration before the workloads are active. Think about how your supply chain works and how to find issues early.
The next time you see CNAPP, CASB, WAAS, CSPM or many of the other phrases, it will be helpful to take a deep breath and realize enterprise security has never been a binary one or zero. It’s never a question of do you have this or that. Framing your needs around workloads, identity, posture, and enterprise can help you better understand your specific needs and put you in a better position when trying to align with these other terms.














