A serious denial-of-service (DoS) vulnerability impacts several industrial automation products from Japanese electrical engineering and software company Yokogawa Electric.
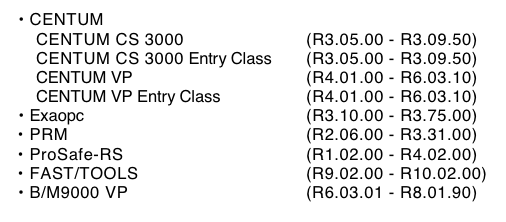
The flaw exists in the Open Communication Driver for Vnet/IP, a real-time plant network system for process automation. The problematic driver is present in several Yokogawa products, including CENTUM CS 3000 and CENTUM VP distributed control systems, the Exaopc OPC interface package, the Plant Resource Manager (PRM) platform, ProSafe-RS safety instrumented systems, the FAST/TOOLS SCADA solution, and the CENTUM VP-based B/M9000 paper quality measurement and control system.
ICS-CERT says the impacted products are used worldwide, mainly in the critical manufacturing, energy, and food and agriculture sectors.
The vulnerability is tracked as CVE-2018-16196 and it has a CVSS score of 7.5, which puts it in the “high severity” category. It’s worth noting that DoS vulnerabilities can pose a serious risk in the case of industrial control systems (ICS), as opposed to IT systems where they are often seen as having a low impact.
Learn More About ICS Vulnerabilities at SecurityWeek’s ICS Cyber Security Conference
The security hole was apparently discovered by Yokogawa itself, which informed Japan’s JPCERT of its existence last month. JPCERT forwarded the information to ICS-CERT in the United States.
The advisories from Yokogawa, ICS-CERT and JPCERT (written in Japanese) reveal that the vulnerability can be exploited by a remote and unauthenticated attacker — even one with a low skill level — to disrupt the communications functionality of the Vnet/IP Open Communication Driver.
Yokogawa has released patches that can be applied to several of the impacted products. Some of the affected software versions have reached end of support and they will not receive patches — the vendor has advised customers to consider upgrading their system to the latest version.
Related: Severe Flaws Found in Yokogawa Switches, Control Systems
Related: Hardcoded Credentials Expose Yokogawa Controllers to Attacks














