By Including The Counterattack in IT Security Strategy Planning, Security Teams Can Quickly Change The Dynamics of a Cyber Attack…
Any competent military commander knows that when put in a defensive position, defense forces are never be able to withstand long and sustained offensive attacks. The assumption that the front line of defense will eventually be breached is also true in the realm of the information security battle of defense.

As an IT defender who protects with network security products, you may never feel confident that your solutions will provide sufficient security protection under all circumstances. The cyber enemy may try and surprise you in so many ways and, if he is persistent and intelligent, will eventually find an attack for which you weren’t prepared. Doubtless, this is exactly where the enemy will focus his efforts. The attack will concentrate on that weakness in order to wear you down and penetrate through all your defense layers.
There is, however, a strategy to address the inherent inferiority of a defending force versus an attacking force: It is called a Counterattack. If network security professionals include the counterattack in their IT security planning, they can quickly change the dynamics of a cyber attack.
The Counterattack
A counterattack is the term used to describe large-scale, usually strategic offensive operations by forces that had successfully halted an enemy’s offensive while occupying defensive positions. A counter-attack is considered to be the most efficient means of forcing the attacker to abandon offensive plans.
The counter attack operation should be well prepared in order to hit the attacking forces precisely in weak spots of their own, thus impeding the attacker’s capabilities, both physical and motivational, in the most effective way possible. These weak spots can and should be identified before and during the battle by field intelligence (in our case, security experts with hands-on experience with the attack tool). There are three main conditions that need to be met in order for a counter offense to be successful:
• The enemy’s weak spots must be successfully identified.
• The defense force must be well trained to conduct a counter attack operation.
• The defense force must successfully halt the enemy’s offense.
In the realm of cyber attacks, the concept of a counterattack operation must also play a major role in the defense strategy against emerging cyber threats. The counter-attack approach could be a game changer, as it enables overcoming limitations in existing defense strategies against cyber attacks.
In Part One of this article, I’ll discuss a cyber attack mitigation strategy, with emphasis on the counterattack operation – an approach to attack mitigation that exhausts the attack source.
Breaching the Perimeter Borders
In the realm of information security, counterattack operations are all about reaching the origin of the attacks and impacting them in a way that will reverse the power relationship in favor of the defenders.
Cyber attackers are becoming more and more persistent. They are capable of harming online businesses, regardless of their motivations, with a wide arsenal of attack techniques and tools. Today’s attackers aim to deny service (DoS attacks), take control or steal information through different attack methods at the network and application levels. This is done through either highly visible large volume attacks or more low-rate and stealthy types of attacks. Sometimes both attack types are used simultaneously in order to ensure success in case one attack vector fails.
Persistent attackers will use different tools aiming to exploit weaknesses in the different layers of defense. Once a weakness is spotted in one of the layers — an effort that sometimes can take days — the attacker will focus on exploiting it to the fullest. Today’s attack operations can recruit an infinite amount of resources such as bot-infected machines, voluntary attackers who take part in larger coordinated campaigns orchestrated by hacktivists, or by non-voluntary attackers unaware their machines have been hijacked. This makes the power relationship between attackers and defenders extremely challenging.
The answer to the question of how on-line businesses and organizations can reduce the probability of becoming a victim of these persistent advanced attacks, or how to resist these attacks in a way that renders them unsuccessful, has a lot to do with the counterattack operation approach.
Ideally, defenders would like to get as close as possible to each attacker and neutralize his ability to generate the attack traffic, thus cleaning the “bad” traffic end-to-end – a very effective way to neutralize DDoS attacks. What if you could create a situation in which the attacker’s machines are slowed down or even halted, thus making the bad guys quit the whole attack campaign for obvious reasons? This last option is possible and can reverse the one-sided power relationship between the attackers and the defenders through a successful counterattack operation.
In order to do this, the defense mechanisms should virtually “breach” the network perimeter borders. The following diagrams illustrate this:
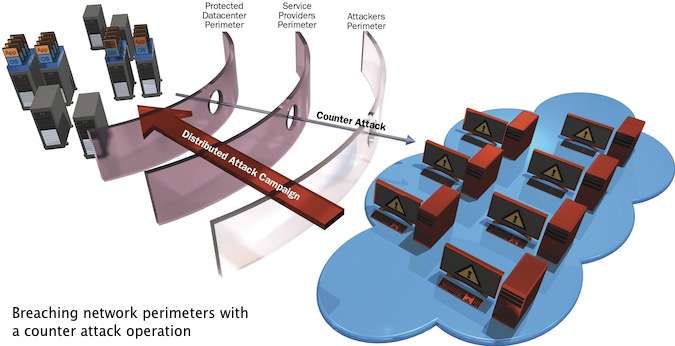
Figure 1: Breaching network perimeters with a counter attack operation
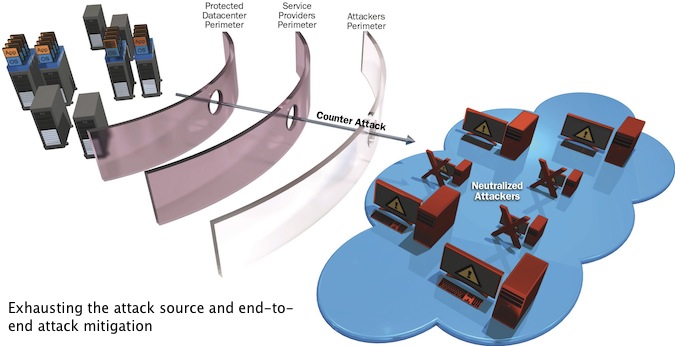
Figure 2: Exhausting the attack source and end-to-end attack mitigation
As shown in the above illustrations, there are a few perimeter borders that the attack traverses from its origin to the target destination. The closer the mitigation process to the attack’s origin, the better the cleaning will be. This is what we define as end-to-end mitigation. Moreover, if the mitigation technique can naturalize the attack tool, through a counterattack technique, the effect becomes much stronger as it essentially “exhausts” the attacker, making him rethink the plausibility of continuing the attack on the target, or launching a similar attack on the target in the future.
The main advantage of the counterattack is that it reaches the source wherever it is, virtually breaching all network perimeter borders. All this is done without the need to physically deploy a network security device in each one of these perimeters.
To summarize, the main advantages of a counter-attack are:
1. Virtually extending the network perimeter of defense up to the attack origin.
2. “Exhausting” the attacker in a way that will make him quit the attack campaign.
3. Reversing the “impossible” power relationships between the attackers and defenders.
In Part Two of this column, I talk about the importance of pattern matching to identify the attack tool hackers may use against your network and how to administer a reverse multi-vulnerability attack campaign against them like a cyber judo chop.















