A Solid Cyber Counterattack Plan Should Be Based on The Pre-defined Actions Associated With Each Attack Tool’s Weakness
In Part One of this column, I covered the concept of making a counterattack a key component in company’s IT defense strategy due to its ability to reverse the power relationship in favor of the defenders. To be effective in a counter attack, defenders ideally would like to get as close as possible to each attacker and neutralize his ability to generate the attack traffic, thus cleaning the “bad” traffic end to end – a very effective way to neutralize DDoS attacks. So what techniques should the counterattack contain?

Effective cyber counterattacks should include the following steps:
• Detect and block the attack.
• Identify the attack tool.
• Locate weaknesses in the attack tool in real-time or based on previous information.
• Launch a counterattack that exploits the attack tool’s weakness.
• Slow down or completely neutralize the attack tool.
Attack detection and blocking steps construe the traditional way of handling cyber attacks. Many attack mitigation tools comprise an important phase in a business’s cyber security defensive strategy; but how do you pivot and take steps that lead to a successful counterattack?
Attack Tool Identification
Identification of the attack tool used as a vehicle to carry the attack campaign is done though pattern matching. There are hundreds of attack tools used in today’s market, each one capable of generating different types of attacks. Each attack tool has some kind of fingerprint, invariant to the attack content itself, which can be detected through different pattern matching algorithms.
Identifying an Attack Tool’s Weaknesses
Conducting research can expose inherent weaknesses in each attack tool. Counterattack-motivated research will find ways of neutralizing the tool in a “passive”, non-intrusive way. There are different methods to manually or automatically discover tool weaknesses, which is a conversation for another day. One example of a weakness, however, is the TCP congestion control mechanism.
Attack tools that rely on the operating system TCP congestion control algorithm usually possess a weakness that a counterattack operation could exploit to exhaust the attacking machine’s stack and CPU resources. The TCP congestion control and avoidance algorithms are designed to transfer larger chunks of traffic (packets) as long as no traffic congestion is identified (e.g., no packet drops, relatively short round trip time, etc.).
If, on the other hand, the mechanism identifies congestion, then the mechanism will automatically “slow down” the data transmission rate for each connection and will gradually accelerate it once the congestion ceases to exist. This process is called “slow start”. This process also makes sure the data transmission takes longer.
Imagine an attack tool that tries to generate new attack connections, filled with data, as fast as the OS allows. If we can create a situation in which the “slow-start” process will kick in on every TCP connection, then the lifetime of each attack connection will become longer. This will create an increasing number of simultaneous connections that will eventually exhaust the OS memory and CPU resources of the attacking machine. This means that a good counterattack operation needs to create a condition in which the slow start process will be activated on any connection that the attack tool tries to generate, over and over again, thus slowing down or even crashing the attacker’s machine.
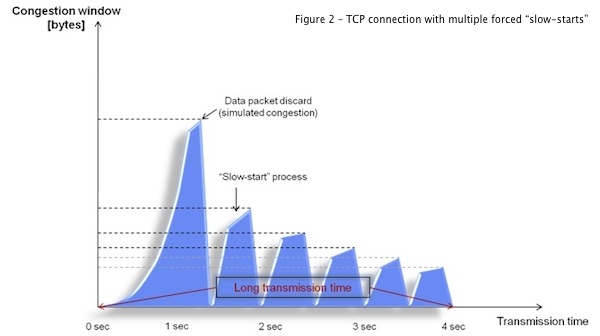
The following diagrams illustrate the slow start process and its impact on a single connection’s lifetime:
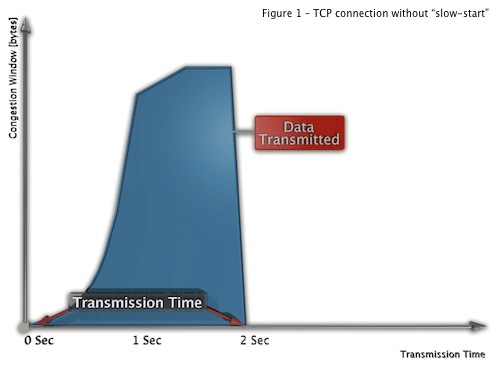
Figure 2 shows what happens when we choose, to drop a data packet inside a connection in order to simulate a congestion condition. In this case, the “slow-start” process is initiated, meaning that it will take more time to transmit the same amount of data (Figure 1).
Counterattack Generation
The congestion simulation above is one example of a counterattack that exploits a weakness in an attack tool using the TCP congestion control mechanism. Different counterattack actions should be generated based on the identification of the attack tool and the attack that it launches. Actions such as TCP reset, application challenge/response, manipulation of the window size (e.g., “tarpit” actions) and others are all applicable counterattack actions.
If the attack and attack tool are identified correctly and mapped to the right counter attack action then the final result is neutralization of the attack tool.
Conclusions
The aim of a cyber counterattack can be achieved by the following:
• Remove the inherent advantage that offensive forces usually have over defense forces.
• Exhaust the attackers’ resources, physically and mentally, wherever they are.
• Clean the attack traffic end-to-end, breaching all network perimeters borders.
Achieving these goals is far from trivial. It requires a strong security research team that is on top of the most advanced attack tools, security products that can accurately identify the attack and the tool that carries it, and is then able to generate the counterattack action based on the pre-defined counterattack actions associated with each attack tool’s weakness.
The counterattack provides, perhaps for the first time, an opportunity to gain a real advantage over financially motivated cybercrime organizations, hacktivists, and other attackers with malicious intent. Make it part of you IT security strategy.
Related Reading: Security Is Not Just About Defense [Part One]














