The abundance of security solutions flooding the market (and IT racks) has not resulted in any a strong confidence for preventing cyber-attacks.
To support that notion, here are a few stats that provide an interesting perspective on the current state of cybersecurity:
• 400+ companies presented at the recent RSA conference.
• About 10% of that number – 40-50 security products of different types – are typically deployed at any organization.
• When surveyed, only 75% of security professionals were confident in their team’s ability to detect and respond to incidents. While this may not sound that bad, among those 75 percent, 6 in 10 did not believe their staff can handle anything beyond simple cybersecurity incidents.
If you’ve been around the security industry the past years, you’re probably not surprised. Companies are adding more and more security solutions, some overlapping, with uncoordinated responses. The result is de-optimization of cyber security investment, accompanied by unmanageable noise, alerts and maintenance tasks. Network security engineering personnel are busy updating policies of multiple security products and SOC teams are sifting through alerts, identifying false positives, and attempting to tune SIEM and other monitoring and correlation tools to each event. If all this does not sound familiar yet, go ahead and read my last article, Why Attack Campaigns Like Security Silos.
Can the rules of the game be changed?
Let me introduce the concept of a “Virtual Security box.”
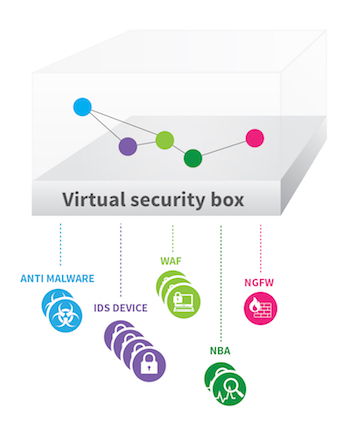 Compute and network virtualization are not exactly a new thing. But just like the virtualization of servers, storage devices, and network devices – a virtual security box decouples configuration complexity associated with too many security solutions, optimizes resources and policies and allow faster, smarter, and well-coordinated response to advanced attacks campaigns. And all this, without being forced to consolidate solutions and get locked into a limited number of vendor solutions.
Compute and network virtualization are not exactly a new thing. But just like the virtualization of servers, storage devices, and network devices – a virtual security box decouples configuration complexity associated with too many security solutions, optimizes resources and policies and allow faster, smarter, and well-coordinated response to advanced attacks campaigns. And all this, without being forced to consolidate solutions and get locked into a limited number of vendor solutions.
Virtual Security Box – Orchestrating All Security Policies
How would this work? First, the Virtual Security Box dynamically integrates with existing security products – whether it’s reputation, anti-malware, IDS/IPS, user and network behavior analysis, firewalls, antivirus or others. It transforms all security products and services into virtual security resources, decoupled from the underline security physical infrastructure. To begin with, this provides a unified playground with a single security language, rather than disparate silos, each with its own rules, terminology etc.
What are the other characteristics of the Virtual Security Box?
• Mix and match. The Virtual Security Box analyzes and rate the quality of each of the existing security products. It then selects and assigns the most relevant and best security resource for each task, completely decoupled from the underline physical security infrastructure. For example, to protect against a privileges escalation attack, it may select Product A to execute the ‘brute-force’ protection policy, and Product B to execute the ‘privilege escalation intrusion’ protection and ‘pre-attack probes’ policy.
• Orchestration. A Virtual Security Box can create and update activity flows between logical resources and thus transform the siloed security infrastructure into a cyber security system that can react much faster and in a more efficient manner to emerging advanced attack campaigns. It can instantly identify and asses the risk and activate the right resource at the right time.
Mitigating Advanced Attack Campaigns and Tracking ROI
The underlying premise of the Virtual Security Box – a responsive, cross-product mitigation approach, best matches the characteristics of advanced attack campaigns, which are multi-vector, prolonged and adaptive to the defenses they encounter. This brings forward several benefits:
• Collaboration and reduced time to mitigate. Different IT groups can simultaneously on the same virtual box to provide the best solution, each using its own permission. Network security can handle the logical rules associated with integration of firewalls resources; application security IT teams can manage logical rules associated with anti-malware, DB and WAF related security resources; and the incident response teams can be responsible for analyzing and responding to events.
• Maximizing investment with no vendor lock-in. The Virtual Security Box optimizes the existing security infrastructure. It eliminates the need to work with very few, or a single vendor, in order to resolve the response chaos common in SOCs.
• Tracking ROI of each tool. By virtualizing and then orchestrating all security tools under a single umbrella, the Virtual Security Box can provide visibility into the contribution of each towards the discovery and mitigation of threats. A CISO can measure the ROI of each of the security assets, quantitatively evaluating vendor claims. For example, over a period of six months, the Virtual Security Box may have been using an anti-malware logical resource, but it may discover that the anti-malware product policy that was most dominant in serving this virtual security function was from vendor one vs another.













