Researchers from IOActive and Embedi have conducted an analysis of SCADA mobile applications from 34 vendors and found vulnerabilities in a vast majority of them, including flaws that can be exploited to influence industrial processes.
Two years ago, researchers Alexander Bolshev and Ivan Yushkevich analyzed 20 mobile apps designed to work with industrial control systems (ICS) software and hardware. At the time, they had found roughly 50 security issues – at least one in each application.
Bolshev, who now works for IOActive, and Yushkevich, currently an employee of Embedi, have once again decided to analyze mobile applications used for supervisory control and data acquisition (SCADA) systems in an effort to determine how the landscape has evolved now that the Industrial Internet of Things (IIoT) has become more prevalent.
This time, the experts randomly selected SCADA applications offered on the Google Play Store by 34 vendors – in most cases different than the ones tested back in 2015. The analysis focused on the client apps and backend systems, and it targeted both local and remote applications.
Local applications are typically installed on the tablets used by engineers and they connect directly to industrial devices via Bluetooth, Wi-Fi or a serial connection. Since these programs can be used to control devices such as PLCs, RTUs and industrial gateways, they are typically only used within the plant perimeter, which is considered safe. Remote applications, on the other hand, allow engineers to connect to ICS via the Internet and private cell networks. While in most cases they are only designed for monitoring processes, some of them do allow users to control processes.
Bolshev and Yushkevich set out to find vulnerabilities described in the 2016 OWASP Mobile Top 10 list. These flaws can allow attackers with local or remote access to a device – and ones in a man-in-the-middle (MitM) position – to directly or indirectly influence an industrial process, or trick an operator into performing a harmful action.
Apps from both independent developers and major vendors were tested, which led to the discovery of 147 vulnerabilities in clients and their backend systems.
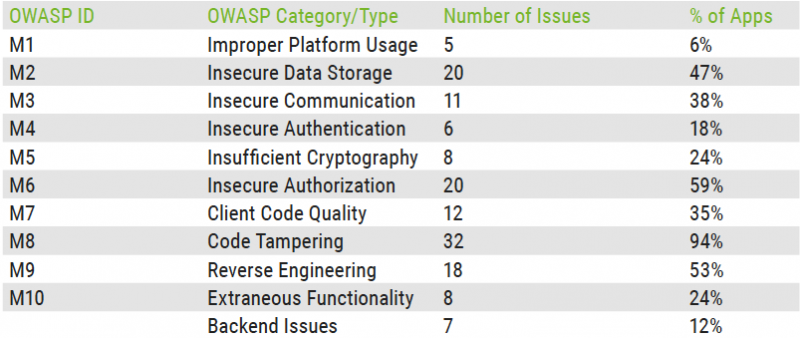
Researchers found that all but two of the applications failed to implement protections against code tampering. The two apps that had such a mechanism only implemented a basic root detection feature. It is easier for malicious hackers to exploit vulnerabilities on rooted Android devices and some malware families are designed to root smartphones and tablets.
Related: Learn More at SecurityWeek’s 2018 Singapore ICS Cyber Security Conference
More than half of the tested applications also lacked secure authorization mechanisms – only 20 percent of the local apps implemented an authorization system correctly. The most common problems are the lack of password protection and the presence of a “remember password” feature, which defeats the purpose of setting password protection.
The experts also found that more than half of the apps lacked code obfuscation and other mechanisms designed to prevent reverse engineering. Allowing attackers to reverse engineer an application makes it easier for them to find and exploit vulnerabilities.
Nearly half of the tested apps also failed to store data securely. Data is often stored on the SD card or on a virtual partition, and it’s not protected with access control lists (ACLs) or other permission mechanisms.
Unsurprisingly, more than one-third of the analyzed applications failed to secure communications, including via poor handshakes, incorrect SSL versions, and cleartext data transmission. Researchers noted that their tests did not cover applications using Modbus and other ICS protocols, which are insecure by design.
As for backend issues, researchers discovered various types of vulnerabilities, including SQL injection, memory corruption, DoS, and information leakage flaws.
Back in 2015, Bolshev and Yushkevich predicted that the problems they had found would disappear in the future as a result of the rapidly developing nature of mobile software and the growth of IoT. However, their predictions have not proved to be correct, with the latest tests showing that more than 20 percent of the discovered issues allow malicious actors to misinform operators and influence industrial processes.














