Supervisory control and data acquisition (SCADA) systems, particularly human-machine interfaces (HMI), can be a tempting target for malicious actors, but it takes vendors, on average, 150 days to patch vulnerabilities in these types of products, according to a new report from Trend Micro and the Zero Day Initiative (ZDI).
The report published on Tuesday is based on the analysis of hundreds of vulnerabilities documented in 2015 and 2016 by ICS-CERT and ZDI.
Researchers pointed out that attackers may target the HMI of a SCADA system for several reasons. Since HMI is a critical component in the management of industrial systems, including critical infrastructure, it can provide access to information that may be highly valuable in a sophisticated attack.
Attackers can also cause physical damage to SCADA equipment once they have compromised the HMI. Furthermore, malicious actors could leverage the HMI to disable alarms and notifications designed to alert operators of dangerous configurations or values.
Since HMIs are typically Windows-based applications rather than web-based apps, vulnerabilities such as cross-site scripting (XSS) and cross-site request forgery (CSRF) are less common. The most common types of flaws uncovered in the past two years are related to lack of authentication/authorization and weak default configurations (23%), memory corruption bugs (20%), credential management vulnerabilities (19%), and code injections (9%).
The average time from disclosure to the release of a patch has not improved much in the past four years. While there are some vendors that manage to patch SCADA vulnerabilities within one week of disclosure, the average time has been roughly 150 days in 2015 and 2016.
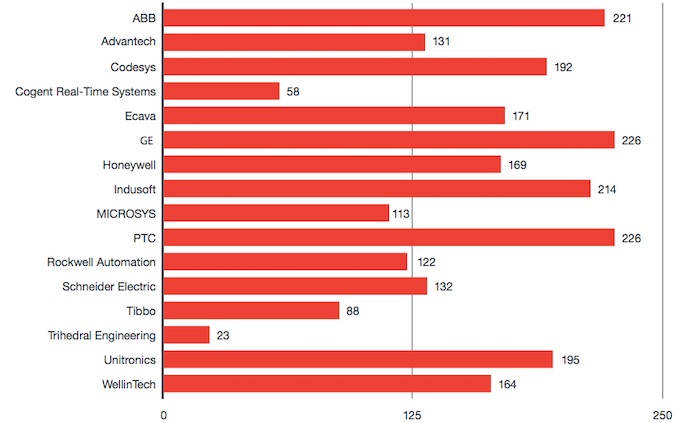
Experts pointed out that some smaller vendors, such as Cogent Real-Time Systems and Trihedral Engineering, patch vulnerabilities faster, while larger companies, such as ABB and GE, have an average response time of more than 220 days.
Compared to other industries, SCADA vendors are roughly at the same level as cybersecurity firms when it comes to how fast they patch vulnerabilities. Vendors of popular software, such as Microsoft, Apple, Oracle and Adobe, have a response time of under 120 days, while business software developers are significantly slower, with an average of 189 days.
Trend Micro’s report includes case studies for each type of vulnerability affecting SCADA systems. The case study for memory corruption vulnerabilities describes a buffer overflow in Advantech’s WebAccess HMI, which could have been exploited to execute arbitrary code with elevated privileges.
As for credential management issues, which include hardcoded passwords and insufficiently protected credentials, the security firm shared an analysis of the MDS PulseNET product from General Electric (GE).
The case studies also cover code injections in Cogent DataHub, and authentication and authorization-related flaws in Advantech WebAccess and Siemens SINEMA Server.
The complete report, titled “Hacker Machine Interface – The State of SCADA HMI Vulnerabilities,” is available for download in PDF format.
Related Reading: Non-Targeted Malware Hits 3,000 Industrial Sites a Year
Related Reading: Overhyped Media Reports Bad For ICS Security
Related Reading: Exploring Risks of IT Network Breaches to Industrial Control Systems














