Since it’s the second Tuesday of the month, enterprise software maker SAP has released its Patch Day Security Notes for December 2015.
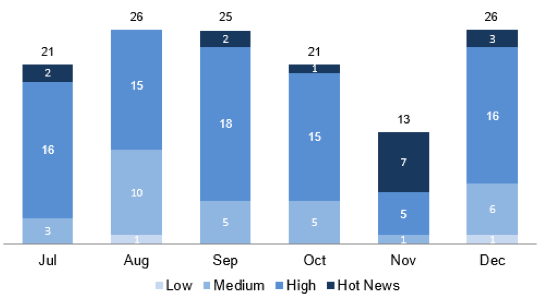
The company has addressed a total of 26 issues, including 19 new vulnerabilities and seven updates to previous patches. Of the 26 vulnerabilities, three have been rated “hot news” and 16 have been classified as “high” severity.
The patches fix four cross-site scripting (XSS), three information disclosure, four missing authorization and authentication check, and two denial-of-service (DoS) vulnerabilities. Remote code execution, hardcoded credentials, SQL injection, cross-domain redirection, and cross-site request forgery (CSRF) issues — one of each — have also been resolved.
According to ERPScan, a company that specializes in securing SAP and Oracle business-critical software, the most urgent patches based on their CVSS score are for previously released updates. These issues include an OS command execution vulnerability in NetWeaver Search and Classification (TREX) and NetWeaver Business Warehouse Accelerator (BWA), a DoS flaw in BusinessObjects BI, a remote command execution bug in 3D Visual Enterprise Author, Generator and Viewer, and an incorrect configuration issue in HANA.
Patches for a couple of medium severity issues reported by ERPScan, an authentication bypass in SAP Mobile Platform and an implementation flaw in SAP LogViewer, have also been updated.
Eight of the patched vulnerabilities fall under the “other” category, which experts say is not unusual for complex business applications like SAP.
“Configuration and other unusual issues in SAP are 5 times more common than in traditional products, thus a significant part of security measures falls on shoulders of administrators,” ERPScan explained in a blog post.
In September, ERPScan reported finding a serious vulnerability in SAP Afaria, a mobile device management (MDM) solution used by 6,300 enterprises to manage 130 million mobile devices. The weakness could have been leveraged by hackers to send out malicious administrative messages designed to lock or wipe the mobile devices used by a company’s employees.
Related Reading: Serious Vulnerabilities Patched in SAP Products
Related Reading: Flaw in SAP Firm’s XSS Filter Exposed Many Sites to Attacks














