SAP on Tuesday released its security updates for August 2018. The latest round of updates includes over two dozen patches, but none of them are for critical (hot news) vulnerabilities.
The German software giant has provided 27 SAP Security Notes, including 14 Patch Day Notes and 13 Support Package Notes. Seven of the total are updates to previously published patches.
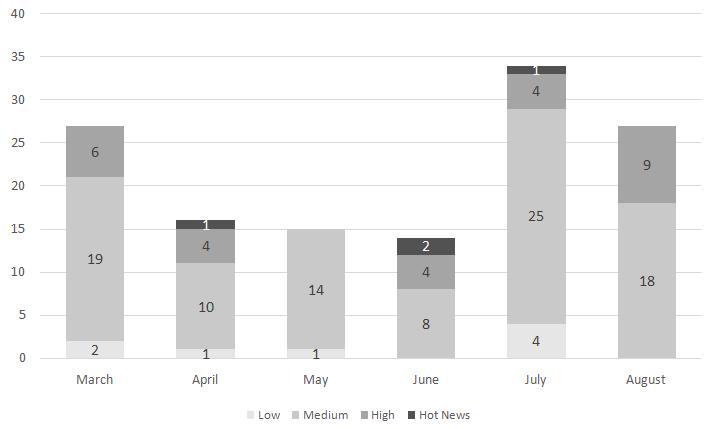
Nine of the patches address high severity flaws, including two discovered by researchers at Onapsis, a company that specializes in securing Oracle and SAP applications.
“One [Security Note] fixes two SQL Injection vulnerabilities in SAP BusinessObjects. Basically, an attacker with a low privileges session can inject data and extract information that he should not be able to. The other vulnerability fixes two bugs found in SAP HANA XSA,” Onapsis said in a blog post detailing this month’s patches.
“The [SQL injection] issues were found in the frontend webserver of the Central Management Console (CMC). One of these SQLi is a blind SQLi, and the other a regular SQLi blind boolean-based SQLi vulnerability,” the company added. “These SQLi vulnerabilities […] allow an attacker without privileges to get information from the Central Management Server System Database. As described, it is sensitive infrastructure information related to the BusinessObjects Enterprise platform, its structure and configuration.”
ERPScan, another company specializing in securing SAP applications, noted that six of the flaws resolved in the past month are implementation issues, while another six have been described as missing authorization checks.
ERPScan has provided a brief description for three of the most serious vulnerabilities patched by SAP with the August updates. The security holes, all rated “high severity,” include the SQL injection flaws found by Onapsis in BusinessObjects (CVE-2018-2447), a missing authorization check in the SAP SRM MDM Catalog (CVE-2018-2449), and a memory corruption flaw in the BusinessObjects Business Intelligence platform that can lead to arbitrary command execution (CVE-2015-5237).
“An attacker can use [CVE-2018-2449] to access a service without any authorization procedures and to use service functionality that has restricted access. This can lead to an information disclosure, privilege escalation, and other attacks,” ERPScan said.
Related: SAP Releases Critical Updates for Two Security Notes
Related: 13 Year-Old Configuration Flaw Impacts Most SAP Deployments














