A survey conducted by the SANS Institute shows that the budgets allocated by organizations for the security of industrial control systems (ICS) and other operational technology (OT) has decreased significantly in 2023 compared to the previous year.
For its 2023 ICS/OT Cybersecurity Survey (PDF), SANS surveyed over 700 individuals from every continent. The respondents represent organizations of all sizes and a wide range of industry verticals, including energy, IT, and government.
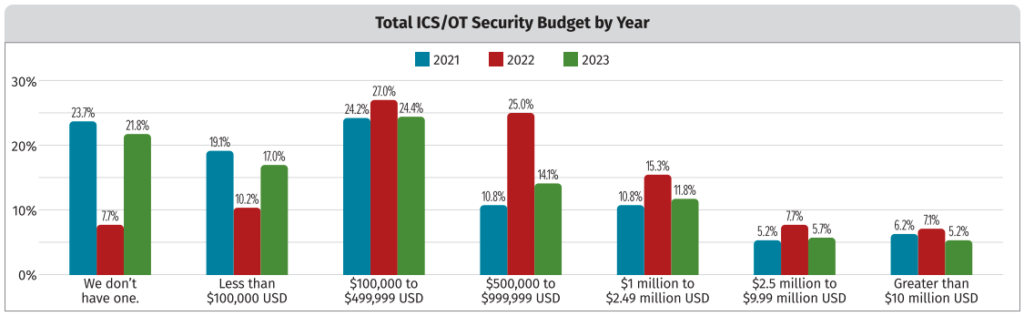
When asked about their ICS/OT cybersecurity budgets, more than 21% said they don’t have one, a significant increase from the 7% in 2022. SANS has been monitoring budgets across several ranges and most of them have decreased compared to the previous year.
Over the next 18 months, over 60% of organizations plan on investing in products that will help them increase visibility into control system assets and configurations. Thirty percent said they plan on investing in anomaly and intrusion detection tools for control system networks.
“Although some facilities may be in a low budget cycle for 2023, it’s imperative that they continue focusing on their ICS cybersecurity roadmap,” SANS recommends. “This means spending on what will provide the highest return to reduce the highest known risks. Security awareness, leveraging ICS tools from trusted sources for assessments (such as from MITRE), a risk-based approach to vulnerability management, and alignment with the five ICS cybersecurity critical controls, are solid places to shift the strategy for 2023.”
The survey also found that in many cases threat actors continue to gain access to ICS/OT systems after compromising IT systems. This was named as an initial attack vector by 38% of respondents, followed by engineering workstations, external remote services, and exploited internet-exposed applications.
When asked about their penetration testing efforts, more than half of respondents said they target Level 3 and the DMZ of the Purdue Model. Level 3 includes customized OT devices that manage production, and the DMZ includes firewalls, patch management servers, application servers, and remote access servers.
More than 40% of respondents said they also target Level 2 (HMI and SCADA systems) and Level 4 (enterprise network).
“A practical penetration test of a real-world scenario could be to emulate TTPs across IT into ICS, starting the test with an established IT foothold, such as in Level 4, then attempt to move into the ICS network DMZ or lower (such as Level 3) toward traditional operating system-based HMIs or toward engineering workstations,” SANS said in its report.
As for the use of threat intelligence to improve their OT defense posture, 61% of respondents said they rely on publicly available information and 30% on security vendor-provided intelligence. More than 40% of respondents also leverage information sharing partnerships, IT threat intelligence, and ICS manufacturer or integrator intelligence.
The SANS report also covers the use of cloud services for ICS/OT systems, incident response practices, and patch management.
Learn More at SecurityWeek’s ICS Cyber Security Conference
The leading global conference series for Operations, Control Systems and OT/IT Security professionals to connect on SCADA, DCS PLC and field controller cybersecurity.
October 23-26, 2023 | Atlanta
www.icscybersecurityconference.com
Related: MITRE and CISA Release Open Source Tool for OT Attack Emulation
Related: Every Network Is Now an OT Network. Can Your Security Keep Up?
Related: ICS Computers in Western Countries See Increasing Attacks: Report
















