Industrial control system (ICS) computers in the Western world have been increasingly attacked, but the percentages are still smaller compared to other parts of the globe, according to Kaspersky’s latest ICS threat landscape report.
In the first half of 2023, Kaspersky blocked threats on 34% of the ICS computers protected by its products, with the second quarter seeing the highest quarterly level since 2019.
Industrial systems from which Kaspersky collected data include SCADA servers, historians, OPC systems, engineering and operator workstations, HMIs, computers used to manage industrial networks, and devices that are used to develop industrial automation software.
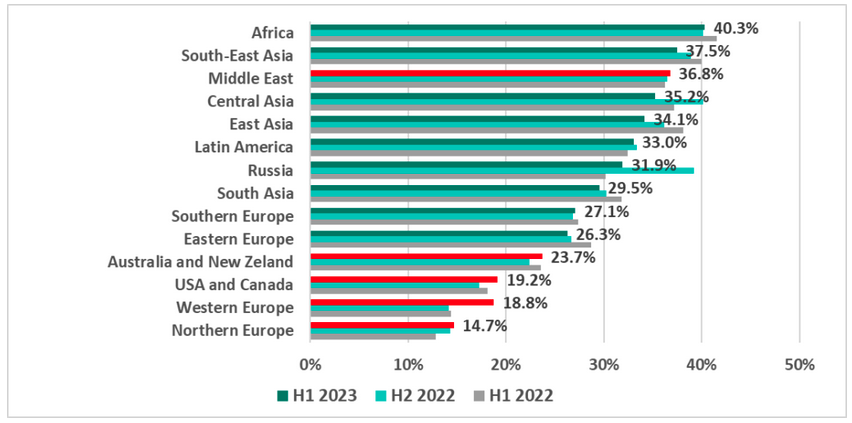
In the first half of the year, Western Europe, the US and Canada, Australia and New Zealand, and Northern Europe saw the highest increase in attack percentage points. This is interesting because, as Kaspersky pointed out, these are the regions that historically have had the lowest percentages of ICS devices on which malicious elements were blocked.
The biggest increase was seen in Western Europe, where the percentage of attacked ICS devices increased from 14.2% in H2 2022 to 18.8% in H1 2023.
On the other hand, Western countries still saw the lowest attack percentages. The highest percentages of attacked devices were in Africa, Southeast Asia, Middle East, Central Asia, East Asia, Latin America and Russia.
“Blocked denylisted internet resources, and malicious scripts and phishing pages were the biggest contributors to this increase in the historically safer regions,” Kaspersky explained.
Denylisted internet resources can include email addresses sending spam, malicious websites, and potentially malicious apps that the user is trying to download.
Denylisted internet resources was the only category that saw growth in the first half of the year.
“The percentage of ICS computers on which threats in this category are blocked has grown for the second half-year in a row,” Kaspersky noted in its report, adding, “Until 2022, denylisted internet resources had topped the list of threat categories, but in 2022, they took second place to malicious scripts and phishing pages, which still remain at the top of the list. Yet, the values for these two types of threats were converging.”
Learn More at SecurityWeek’s ICS Cyber Security Conference
The leading global conference series for Operations, Control Systems and OT/IT Security professionals to connect on SCADA, DCS PLC and field controller cybersecurity.
October 23-26, 2023 | Atlanta
www.icscybersecurityconference.com
Related: Drop in Insider Breaches Drives Decline in Intrusions at OT Organizations
Related: Engineering Workstations Used as Initial Access Vector in Many ICS/OT Attacks: Survey
















