Resilient “SMSZombie” Exploits China Mobile’s Payment System – Over 500,000 Android Devices Infected, Firm Says.
Researchers from mobile security firm TrustGo have recently discovered a new, resilient mobile threat targeting Android phones that is said to have infected roughly 500,000 devices, mainly in China.
 Called “SMSZombie”, the malware is stubborn and hard to remove, but users outside of China have little to worry about with this latest discovery. The prime function of the mobile malware is to exploit a vulnerability in the mobile payment system used by China Mobile, making it of little value to the fraudsters outside of China.
Called “SMSZombie”, the malware is stubborn and hard to remove, but users outside of China have little to worry about with this latest discovery. The prime function of the mobile malware is to exploit a vulnerability in the mobile payment system used by China Mobile, making it of little value to the fraudsters outside of China.
According to TrustGo, the malware is being spread through online forums and has been found in several packages on China’s largest mobile app marketplace, GFan. TrustGo has contacted GFan, but so far, the apps are still readily available and continue to be actively downloaded.
Cataloged as SMSZombie.A, it was first discovered by TrustGo on Aug 8, Jerry Yang, Vice President of Engineering at TrustGo told SecurityWeek on Saturday.
SMSZombie has been embedded in several wallpaper apps, many of which flaunt provocative titles and nude photos to encourage users to download and install the apps. One such example is an app called, “Android Animated Screensaver: Animated Album I Found When I Fixed My Female Coworker’s Computer”, as well as others using similar titles, TrustGo said.
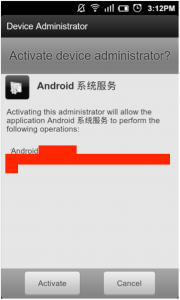
If an Android user downloads the app and sets it as the device’s wallpaper, the app then prompts the user to install additional files. “If the user agrees, the virus payload is delivered within a file called ‘Android System Service,’” TrustGo explained.
If the evil “Android System Service” is installed, the malware attempts to obtain administrator privileges on the device, a step that Yang says cannot be canceled due to the fact that users are essentially forced to click “Activate” because clicking the “Cancel” button just reloads the same dialog box.
“By waiting to deliver malicious code until after installation, this virus is difficult to detect,” said Xuyang Li, CEO of TrustGo.
Calling it a complex and sophisticated form of Android malware, TrustGo said it takes advantage of a vulnerability in the China Mobile SMS Payment process to generate unauthorized payments to premium service providers, and possibly steal bank card numbers and money transfer receipt details.
The malware can remotely control the infected device, Yang said. It enables hackers to remotely control victims’ mobile SMS payments system, allowing them to secretly authorize payments for amount and at any time. “Our guess is that these malware developers have some connection with these premium services,” Yang said.
Additionally, it is set to automatically delete any payment confirmation SMS receipts in an effort to remain undetected.
“Based on our analysis of the code, the malware will monitor users’ SMS messages,” Yang said. “Once it finds any keywords they have defined in the code, they will send these messages to a third party C&C server.”
“Sophisticated malware like this highlights the fact that the openness of the Android platform is a double-edged sword… Users are able to access an amazing breadth and variety of apps, but must take precautions to ensure the apps they want have not been compromised by hackers,” Li said.
As of now, Yang explained, the only way to remove the malware is through a manual process. For the needy, the instructions to remove SMSZombie can be found here.
Yang told SecurityWeek that the TrustGo Security Lab found that SMSZombie doesn’t have a dedicated C&C server. It can send SMS commands to infected devices using random phone numbers. One of the phone numbers they used is +8613145513829 which is from Anhui province, China, he said.
On July 4 of this year, TrustGo detected a piece of malware targeting Android that gained a large install-base rather quickly – infecting 100,000 devices in less than a week.
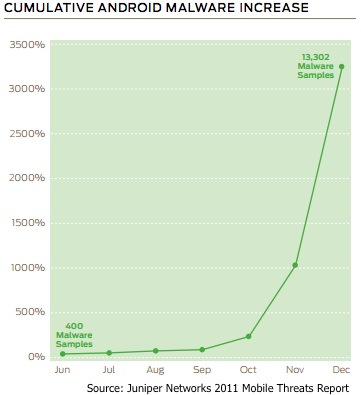
Related Reading: Android Malware Increased 3,325 Percent in Seven Months, Says Juniper Networks