Threat researchers from malware protection firm FireEye have discovered a new type of malware on systems that have been infected with the Gh0st RAT (Remote Access Trojan), with plenty of evidence that suggests that the botmasters for Gh0st are experimenting with new tools.
The Gh0st RAT has been linked to spear phishing attacks that targeted several organizations in Central Tibet earlier this year. In the grand scheme of things, Gh0st is in the same malware family as Poison Ivy, another Trojan used for remote access, and there is speculation that the attackers are in China.
The earlier Gh0st attacks progressed to targeting a wider set of activists, including those using Mac OS systems, but new research has uncovered another tool that expands on Gh0st’s capabilities.
While the victim’s identity isn’t explained, researchers from FireEye have discovered a new malware variant on systems that are infected by Gh0st. The malware, currently named backdoor.ADDNEW, exists side-by-side with Gh0st and has been seen communicating with the same command and control (C&C) server in France with an IP address of 31.33.33.7 through different ports.
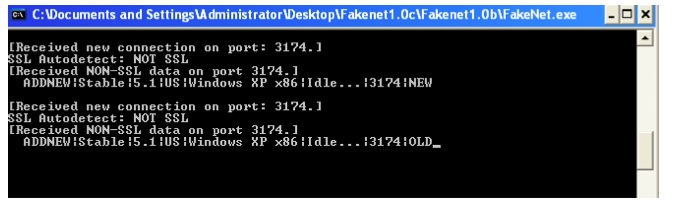
“The Backdoor uses a custom protocol over TCP to communicate to its CnC,” FireEye explained. “Since the domain to which the malware was communicating was down, we used Mandiant’s FakeNet and recorded all the communication. In the picture below you see the very first communication that is sent to the CnC by the infected machine. The “NEW” keyword that is sent back to the CnC lets the CnC know that it is a newly infected machine.”
FireEye researchers noticed that it targets the signons.sqlite database used by Firefox to store passwords. In addition to harvesting credentials from Mozilla’s browser, the malware also opens up a remote link to the system and enables the attacker to launch DDoS attacks.
“There are strings in the binary referencing “DarkDDOSER,” FireEye noted. “One can only speculate if in some way “DarkDdoser” and the Gh0st RAT complement each other.”
For now, FireEye says they are still investigating the malware, and performing more research before they will comment further. This could be the start of something sinister, as the operators of Gh0st expand to inflect additional damage; or it could be something as simple as a botnet being rented out for monetary gain.
Additional details are on the FireEye blog.
















