“Hesperbot” is an Entirely New Banking Malware Family With Advanced Features, Currently Targeting Users In Turkey, The Czech Republic, Portugal and the UK.
Researchers from ESET have uncovered what they are calling a new “Zeus-like Trojan” that is a completely new malware family, but one that packs powerful data-stealing capabilities found in other well-established malware. According to the researchers, the threat is currently targeting online banking users mainly in Turkey, The Czech Republic, Portugal and the United Kingdom.
 Named “Hesperbot” and detected as “Win32/Spy.Hesperbot” by ESET, despite being a new kind of malware, the security firm is calling it a “potent banking Trojan” that features capabilities, including keystroke logging, screenshot and video capture, and even the ability to setup a remote proxy and create a hidden VNC server on the infected system.
Named “Hesperbot” and detected as “Win32/Spy.Hesperbot” by ESET, despite being a new kind of malware, the security firm is calling it a “potent banking Trojan” that features capabilities, including keystroke logging, screenshot and video capture, and even the ability to setup a remote proxy and create a hidden VNC server on the infected system.
“Analysis of the threat revealed that we were dealing with a banking trojan, with similar functionality and identical goals to the infamous Zeus and SpyEye, but significant implementation differences indicated that this is a new malware family, not a variant of a previously known Trojan,” Robert Lipovsky, a malware researcher at ESET, explained in a blog post.
The attackers are using “credible-looking phishing-like campaigns” leveraging trusted brands in order spread the malware, ESET said.
Interestingly, the attackers behind the malware are also attempting to get users to install a mobile component of the malware on their Symbian, Blackberry or Android mobile device. ESET researchers also discovered a component (Win32/Spy.Agent.OEC) used by Hesperbot that harvests e-mail addresses from infected systems and sends them to a remote server.
The configuration files used by the malware’s HTTP interception and injection module specify which online banking websites are to be targeted by each botnet, ESET explained.
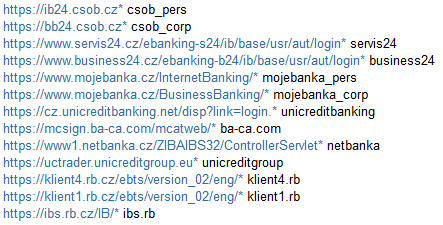
List of Czech Banks Targeted by Hesperbot
According to recent research from Terry Nelms, a researcher at Damballa, 80% of current malware leverages HTTP as the primary access point to corporate networks.
“The Czech malware-spreading campaign started on August 8, 2013,” Lipovsky noted, also saying that the attackers registered the domain www.ceskaposta.net, a similar domain to the real website of the Czech Postal Service, www.ceskaposta.cz.
“It’s probably not surprising that the attackers tried to lure potential victims into opening the malware by sending emails which looked as parcel tracking information from the Postal Service,” Lipovsky said.
In a clever move, the attackers set the fake domain to redirect to the “real website” when opened directly in a web browser.
According to ESET, the country most affected by Hesperbot is currently Turkey, which ESET has found detections in dating priot to August 8.
“Recent peaks in botnet activity were observed in Turkey in July 2013, but we have also found older samples that go back at least as far back as April 2013,” Lipovsky continued. “During the analysis of the samples we found that they were sending debugging information to the C&C – an indicator that these variants were in the early stages of development.”
In the case of the Turkish and Portuguese botnets, ESET noted, the configuration files included HTML web-injects that the malware would insert into the banks’ web-pages when viewed on the infected PC. However, Web-injects were not seen in the Czech configuration file.
“Like many other malware families, Win32/Spy.Hesperbot has a modular architecture,” ESET explained in a separate research document. “As the first step in infection, the victim downloads and runs a dropper component. The dropper is also protected by a custom malware packer and distributed in a ZIP archive.”
ESET explained that the dropper’s role is to inject the main component – ‘core’ – into explorer.exe. The core then downloads and loads additional modules used to carry out malicious actions as detailed in the chart below.
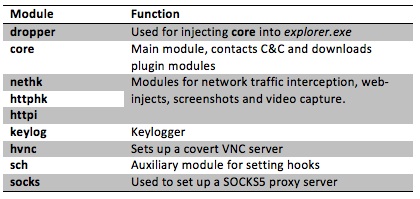
Overall, it’s unclear how many users may have been infected by this new threat, but according to ESET, victims in the Czech Republic have lost “significant amounts of money” at the hands of Hesperbot, with the possibility of similar fate with victims in Turkey and Portugal.
ESET also discovered a variant designed to target users in the United Kingdom, but did not share additional details.
Hesperbot is not the only emerging threat working its way into users’ systems. In late July, another new professional-grade banking Trojan was uncovered that RSA researchers said could soon rival Zeus, SpyEye and Citadel in how effectively it spreads. Dubbed KINS, the banking Trojan has several features in common with Zeus and SpyEye, as well as having a similar DLL-plugin-based architecture.
















