Researchers at enSilo have identified a new method that can be used by hackers to execute a piece of malware on any supported version of Windows without being detected by security products.
The new technique, dubbed “Process Doppelgänging,” is similar to process hollowing, a code injection method that involves spawning a new instance of a legitimate process and replacing the legitimate code with malicious one. This technique has been used by threat actors for several years and security products are capable of detecting it.
enSilo says it has now come up with a similar but more efficient method for executing malicious code, including ransomware and other types of threats, in the context of a legitimate process. Process Doppelgänging abuses the Windows loader to execute code without actually writing it to the disk, which makes it more difficult to detect an attack.
According to researchers, when Process Doppelganging is used, the malicious code is correctly mapped to a file on the disk, just like in the case of a legitimate process – modern security solutions typically flag unmapped code. The method can also be leveraged to load malicious DLLs.
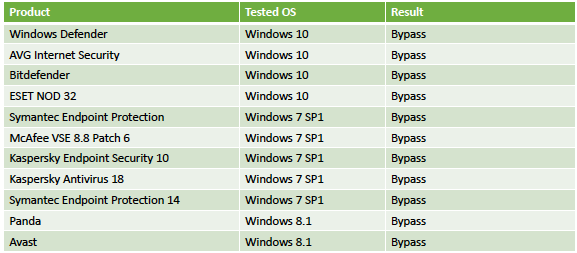
Experts have successfully tested the technique on Windows 7, Windows 8.1 and Windows 10 against security products from Microsoft, AVG, Bitdefender, ESET, Symantec, McAfee, Kaspersky, Panda Security and Avast.
Doppelganging relies on transactional NTFS, which is designed to make it easier for app developers and administrators to handle errors and preserve data integrity. enSilo has found a way to make changes to an executable file via NTFS transactions without actually committing those modifications to the disk. Undocumented functionality of the Windows process loader is then abused to load the modified executable. The changes made to the original file are reverted in order to avoid leaving any trace.
“We overwrite a legitimate file in the context of [an NTFS transaction],” enSilo said. “We then create a section from the modified file (in the context of the transaction) and create a process out of it. It appears that scanning the file while it’s in transaction is not possible by the vendors we checked so far (some even hang) and since we rollback the transaction, our activity leaves no trace behind.”
“There are a lot of technical challenges involved in making it work,”researchers explained. “One of the hardest challenges is that in order to run a process out of a section (not a file on disk) the process needs to be created using NtCreateProces, which means that most of the initialization must be done manually, which requires knowing a lot of undocumented details on process creation.”
enSilo says its products can detect such an attack, which means other vendors can implement detection mechanisms as well, especially if the technique will be exploited in the wild. However, since the method abuses legitimate features, experts say it cannot be patched.
The security firm disclosed its findings this week at the Black Hat Europe conference in London. Technical details and proof-of-concept (PoC) code will be made available shortly.
Related: AtomBombing – The Windows Vulnerability that Cannot be Patched
Related: GhostHook Attack Can Bypass Windows 10’s PatchGuard
Related: BoundHook Hooking Is Invisible to Windows 10’s PatchGuard












