Facebook last week announced that it introduced new settings designed to make it easier for white hat hackers to test the security of its mobile applications.
The social media giant’s mobile applications use certificate pinning and other security mechanisms to protect communications between the application running on a user’s device and Facebook’s servers. While these measures significantly improve security, they also make it harder for researchers to find server-side vulnerabilities in the company’s apps.
That is why — based on feedback it has received from white hat hackers — Facebook has decided to introduce new settings that researchers can enable on their own accounts so that they can analyze network traffic associated with the Facebook, Messenger and Instagram applications when searching for vulnerabilities they can report through the company’s bug bounty program.
This includes configuring a proxy for Platform API requests (on Android), not using TLS 1.3, and allowing user-installed certificates.
Security experts who want to take advantage of these new settings need to first enable them in the web-based version of Facebook and then in the mobile application.
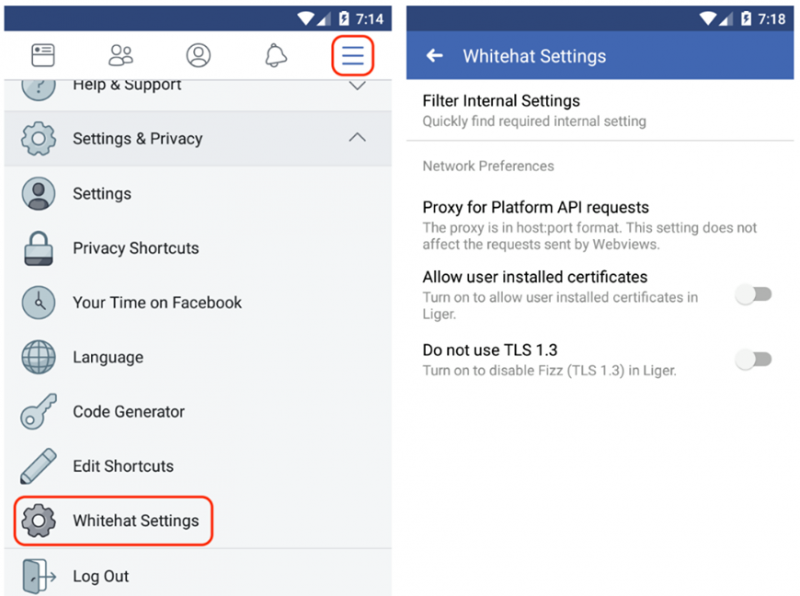
When these “Whitehat Settings” are enabled, a corresponding button will be displayed in the selected app’s menu. In addition, an alert will be shown at the top of the screen to warn that traffic may be monitored.
Facebook recommends that these settings be enabled only during security testing. Detailed instructions for configuring and using the new functionality have been provided by the company.
Facebook reported in December that it had paid out a total of $1.1 million as part of its bug bounty program last year, and a total of $7.5 million since the launch of its program in 2011.
Related: CSRF Vulnerability in Facebook Earns Researcher $25,000
Related: Privacy Fears Raised Over Facebook Messaging Apps Integration
Related: GIF Attack on Facebook Messenger Earned Hacker $10,000
Related: Facebook Says ‘Clear History’ Feature Ready This Year












