MITRE and the DHS’s Cybersecurity and Infrastructure Security Agency (CISA) have announced the release of the “2021 Common Weakness Enumeration (CWE) Most Important Hardware Weaknesses” list.
Composed of the most frequent and critical errors that result in serious hardware vulnerabilities, the list includes a total of 12 entries, with five additional weaknesses that scored just outside the final list also mentioned.
The list is meant to raise awareness of common hardware weaknesses and to help prevent hardware vulnerabilities at the source, MITRE says.
In addition to instructing designers and programmers on how errors can be eliminated during product development, the list can help analysts and engineers plan security testing and evaluation, as well as consumers to ask suppliers to deliver more secure hardware.
The list is also expected to help managers and CIOs assess the progress of their efforts to secure hardware and to decide where resources should be directed to build tools and automation processes to mitigate a wide class of vulnerabilities, MITRE notes.
The final 2021 CWE Most Important Hardware Weaknesses list includes the 12 entries that scored highest during analysis.
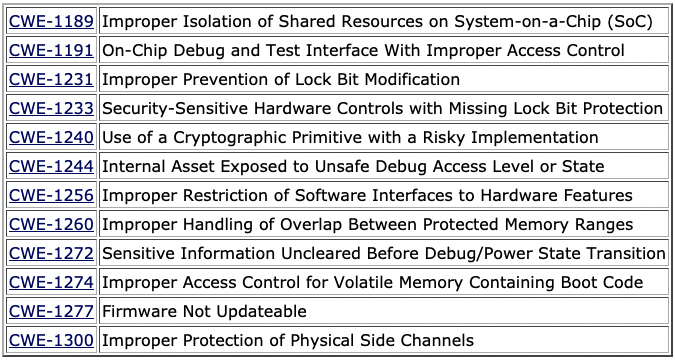
Five other weaknesses (the Hardware Weaknesses on the Cusp) scored just outside of the final list, but risk-decision makers and those performing mitigations should still consider these in their analyses, MITRE says.
Although the methodology used to create the list resulted in a ranking for the 12(+5) CWEs, the hardware team and the Hardware CWE Special Interest Group (SIG) believe that the list should not be viewed as a hierarchical, ordered set when it comes to the importance of each weakness.
“The entries should be thought of as a set of mostly equal hardware weakness concerns based on our methodology,” MITRE notes.
Future versions of the CWE Most Important Hardware Weaknesses are expected to include other entries, aiming to deliver a list considered to be the most useful for the community.
The United States Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the list and the recommended mitigations, to determine which are suitable to adopt.
“The 2021 Hardware List is a compilation of the most frequent and critical errors that can lead to serious vulnerabilities in hardware. An attacker can often exploit these vulnerabilities to take control of an affected system, obtain sensitive information, or cause a denial-of-service condition,” CISA notes.
Related: OWASP Top 10 Updated With Three New Categories
Related: What We Learn from MITRE’s Most Dangerous Software Weaknesses List














