On its 20th anniversary, the Open Web Application Security Project (OWASP) released the final version of their revised Top 10 list of the most critical risks to web applications, which includes three new categories, as well as position shifts compared to the previous report, released in 2017.
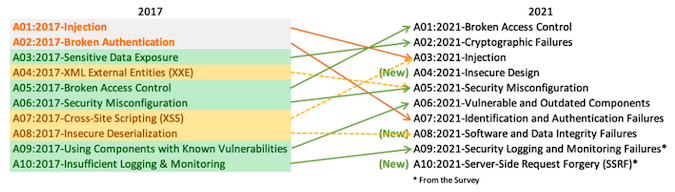
In OWASP Top 10 2021, Broken Access Control has taken the lead as the category with the most serious web application security risks. The category was fifth in the previous version.
There are 34 Common Weakness Enumerations (CWEs) mapped to Broken Access Control, and they had the highest number of occurrences (at roughly 318,000) compared to any other category.
Second in line comes Cryptographic Failures (previously Sensitive Data Exposure), which often results in the exposure of sensitive data or in system compromise. Injection, which now includes Cross-Site Scripting, drops one position to the third place, with its 33 mapped CWEs having roughly 274,000 occurrences.
Focused on risks related to design flaws, Insecure Design is a new category in the Top 10 list this year, but made it all the way up to the fourth position. Security Misconfiguration, which now includes XML External Entities (XXE) bugs, landed on the fifth position, with more than 208,000 occurrences of the CWEs mapped to it.
Sixth on the list is Vulnerable and Outdated Components (previously titled Using Components with Known Vulnerabilities), followed by Identification and Authentication Failures (previously Broken Authentication) on the seventh position, and Software and Data Integrity Failures (also includes Insecure Deserialization) on the eighth.
The Software and Data Integrity Failures category is related to lack of integrity verification in software updates, critical data, and continuous integration/continuous delivery (CI/CD) pipelines.
Ninth on the list is Security Logging and Monitoring Failures (previously Insufficient Logging & Monitoring), with Server-Side Request Forgery (SSRF) emerging as a new category on the tenth position — the risks associated with SSRF are seen as important by the security community, yet data doesn’t show that, OWASP notes.
A major shift from the previous OWASP Top 10 is the focus on the prevalence of CWEs within applications. Rather than focusing on only 30 CWEs, the report is now based on the analysis of almost 400 CWEs, which also resulted in changes to how categories are structured. The OWASP team also focused on root cause types of CWEs, rather than symptoms.
Furthermore, the team mainly took into consideration average exploit and impact scores when compiling the 2021 list, leaving likelihood (Detectability) aside.
“We grouped all the CVEs with CVSS scores by CWE and weighted both exploit and impact scored by the percentage of the population that had CVSSv3 + the remaining population of CVSSv2 scores to get an overall average. We mapped these averages to the CWEs in the dataset to use as Exploit and (Technical) Impact scoring for the other half of the risk equation,” OWASP explains.
For this installment of the OWASP Top 10 list, only eight of the categories were selected from the statistical data, while the remaining two were introduced based on results from the Top 10 community survey.
Related: OWASP Proposes New Vulnerabilities for 2017 Top 10
Related: Cybersecurity Seen as Rising Risk for Airlines After 9/11
Related: Bridging the Cybersecurity Skills Gap as Cyber Risk Increases













