The Israeli Air Force has claimed that in the past week its fighter jets bombed two buildings allegedly used by the cyber unit of Hamas, the Palestinian militant group that runs Gaza.
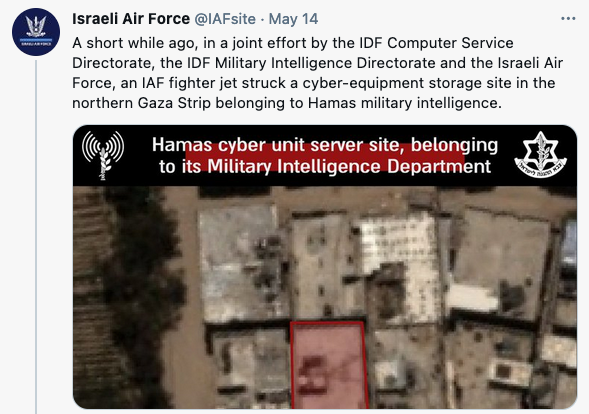
The first announcement was made on May 14, when Israel announced a strike on what it described as a “cyber-equipment storage site of the Hamas terror organization cyber unit.” The Air Force said the building was located in the northern Gaza Strip and it belonged to Hamas military intelligence.
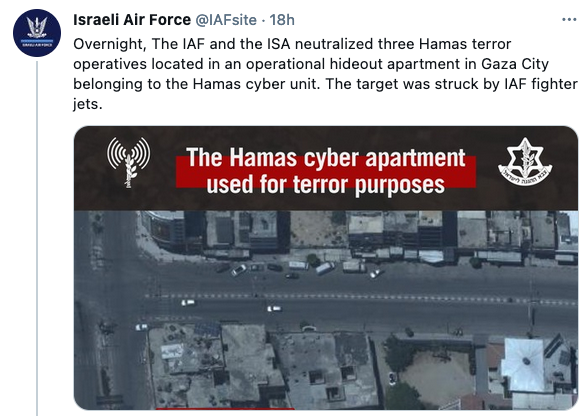
The second announcement was made on May 19, when Israel claimed to have “neutralized three Hamas terror operatives located in an operational hideout apartment in Gaza City belonging to the Hamas cyber unit.”
“The hideout apartment was used by the terror operatives for offensive cyber activity against Israeli targets. These actions are clear proof of Hamas terror activity in the cyber domain,” the Israeli Air Force said on Twitter and its official website.
There has been another escalation of fighting between Israelis and Palestinians. According to Israel, since May 10, Hamas has fired thousands of missiles and Israeli fighter jets struck hundreds of Hamas targets.
This is not the first time Israel has bombed a building allegedly housing Hamas cyber operatives. In May 2019, it launched a similar air strike in response to a cyberattack launched by Hamas. This was the first public report of a cyberattack triggering a kinetic response.
Hamas-linked threat actors have used various techniques to target the Israeli army — soldiers were tricked into installing malware on their devices — and some believe they may have also targeted critical infrastructure in Israel.
Related: Analyzing the UK’s Nuclear Deterrence Theory for Cyberspace
Related: U.S. Army Report Describes North Korea’s Cyber Warfare Capabilities
Related: Digital Warfare: Myanmar’s Cyber Crackdown Explained
Related: UK Warns That Aggressive Cyberattack Could Trigger Kinetic Response














