Iraqi Resistance Group Claiming Responsibility for ‘Here You Have’ Virus May be Based in Spain. Virus gained Momentum but Slowed Quickly.
After intensive investigation of the “Here you have” virus, PandaLabs has discovered that the Iraqi resistance group claiming responsibility, Tariq Bin Ziyad, may be based in Spain.
In a video on YouTube created by the “IRAQ Resistance – Leader of Tarek Bin Ziyad Group,” and posted on Sunday, September 12 by iqziad (26-year-old resident of Spain), a female voice explains the reasons why this group, supposedly based in Spain, has created and distributed the “Here you have” virus (classified by Panda Security as W32/Visal.A.worm, by Symantec as W32.Imsolk.B@mm and by McAfee as W32/VBMania@mm).
The video claims the virus has been created and propagated principally to target the United States for two reasons: to commemorate the 9/11 attacks and to demand respect for Islam, with reference to the threat made by pastor Terry Jones to burn the Koran last week.
“Signs appear that the group responsible for this virus could be residents of Spain, not just because of the information presented on YouTube, but also because of certain aspects of the virus code itself. There is also the link between the name of the group and the Berber general who led the conquest of Al-Andalus,” said Luis Corrons, Technical Director of PandaLabs.
Tariq ibn Ziyad (died in 720) was a Berber commander who led the Muslim invasion of the Iberian Peninsula in the eighth century, conquering Visigoth Hispania, according to generally accepted history based on the Arab chronicles of the 10th and 11th centuries.
Rapid Rise and Rapid Fall
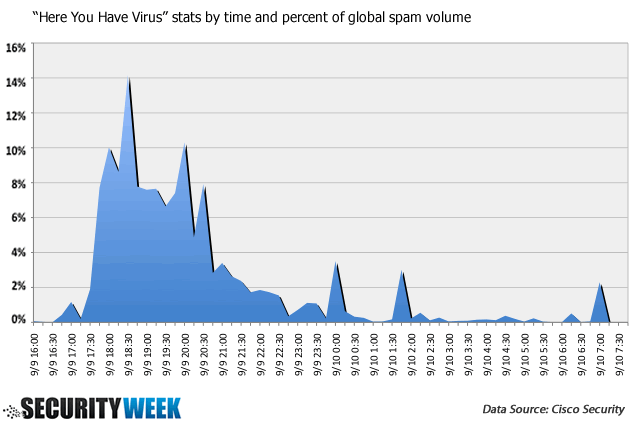
The virus first appeared about a month ago but began spreading rapidly last week.
“The ‘Here You Have’ worm didn’t enter through sources common to most spam, so it never landed in spam traps where it could be tallied and assessed by all the many spam watchers and vendors looking to spam trap data,” said Nilesh Bhandari, Cisco product manager. “It came to a few people’s inboxes looking like legit email and then spread to every contact on every receiver’s list, so the proliferation of emails appeared to be coming from someone known; this caused rapid and broad unfiltered penetration,” Bhandari noted. “As such, these bad emails weren’t landing in spam traps where they could be counted and duly noted by most in that business.”
According to David Harley, Senior Researcher with ESET, despite spreading rapidly for several hours, the propagation slowed rather quickly. “The code wasn’t particularly innovative. Its resemblance to other threatcode, its disabling of security processes, and the use of common vectors such as mass-mailing, Autorun and network shares to spread tend to raise suspicions pretty quickly,” Harley Said. “And of course, the use of filetypes like .SCR (or, more blatantly, .PDF.SCR) is in itself a danger flag that may have tripped generic filtering on secondary infection, even though the initial binary wasn’t mailborne. Additionally, the hosting sites were taken down pretty fast, so the actual malicious files were already unavailable when much of the world (Europe, mostly) started to wake up,” Harley added.