Threat intelligence and incident response firm Volexity has started seeing widespread exploitation of the recently disclosed Ivanti Connect Secure VPN appliance vulnerabilities.
Volexity warned on January 10 that it had seen threat actors — a group tracked as UTA0178 and likely linked to China — exploiting two Ivanti VPN zero-day vulnerabilities in an attempt to gain access to internal networks and steal information.
The vulnerabilities are an authentication bypass flaw tracked as CVE-2023-46805 and a command injection issue tracked as CVE-2024-21887. Chaining the two enables a remote, unauthenticated attacker to execute arbitrary commands on the targeted appliance.
While initially the attacks were highly targeted, widespread exploitation appears to have now begun. Volexity scanned roughly 50,000 IPs associated with Ivanti VPN appliances and found that more than 1,700 were compromised.
The hacked devices belong to organizations in the government, military, telecoms, defense, tech, banking, finance, accounting, consulting, aerospace, aviation and engineering sectors. They include small businesses and Fortune 500 companies.
Victims were seen all around the world, but the highest percentage appears to be in the United States, followed by Europe.
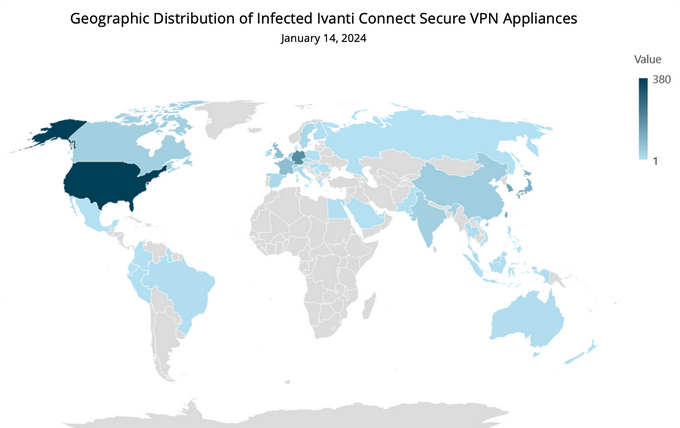
Volexity noted that the actual number of compromised systems is likely higher than what its scans discovered.
“Volexity assesses with medium confidence that this widespread exploitation was undertaken by UTA0178. This assessment is based on the use of an identical webshell to that used in the previous exploitation, and the speed at which it was undertaken following publication of details relating to the exploit,” the cybersecurity firm said.
While UTA0178 seems to be behind many attacks, other threat actors are also trying to exploit the Ivanti product vulnerabilities, including one tracked by Volexity as UTA0188.
Some exploitation attempts are likely the work of the cybersecurity community. Researcher Kevin Beaumont, who has dubbed the Ivanti vulnerabilities ConnectAround, has also been conducting scans.
Ivanti made available mitigations on January 10, but patches are only expected to become available starting the week of January 22.
Mandiant has also analyzed the attacks involving exploitation of CVE-2023-46805 and CVE-2024-21887, linking them to a cyberspy group it tracks as UNC5221.
The company has identified five malware families deployed by the hackers, including webshells, droppers, backdoors and information stealers named ThinSpool, LightWire, WireFire, WarpWire and ZipLine. Mandiant saw indications that the hackers had taken steps to maintain access to high-value systems even after the release of patches by Ivanti.
Related: Second Ivanti EPMM Zero-Day Vulnerability Exploited in Targeted Attacks
Related: Exploitation of Ivanti Sentry Zero-Day Confirmed
Related: Ivanti Ships Urgent Patch for API Authentication Bypass Vulnerability

















