Google on Tuesday announced that G Suite users can now log in on platforms that don’t directly support security keys using security codes generated by their security keys.
Security keys, which are two-factor authentication (2FA) devices, are considered highly efficient for protecting accounts against phishing and other types of threats. However, they often don’t work on legacy platforms that do not support FIDO protocols or applications such as Internet Explorer, Safari and iOS apps.
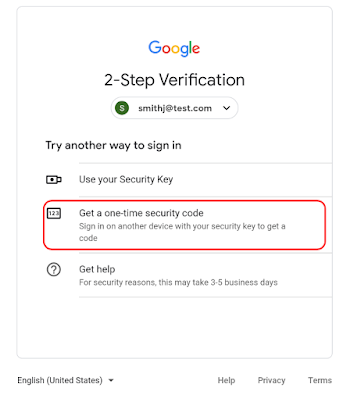
G Suite administrators and end users can now use their security keys to log in on platforms that cannot communicate with a security key directly. If the new feature is enabled, users will see a “Having trouble” or “Try another way” option on the 2-step verification (2SV) page. If they select one of these options, they will be allowed to either use their security key directly (if supported) or obtain a one-time security code that they can use to log in.
The security code process involves connecting the security key to a compatible system and visiting a specific URL from where they can obtain the one-time code that must be entered in the uncompatible service.
“For example, a user may need to access a web application that federates their Google identity, but only works on Internet Explorer 11. While the browser can’t communicate with a security key directly, the user can open a Chrome browser and generate a security code, which can then be entered in Internet Explorer to gain access to the application,” Google explained in a blog post.
On domains that enforce the “Only security key” policy (i.e., they only allow logins with a security key), the new feature can be enabled by admins by accessing Admin Console > Security > Advanced security settings and selecting “Users may utilize security code.” The new feature is being rolled out gradually over a period of up to 15 days for these domains starting with July 8.
The feature will be enabled by default on domains that enforce “Any” or “Any except verification codes via text, phone call” policies. The rollout has already started for these domains and it will take up to 15 days.
Related: Google Turns on G Suite Alerts for State-Sponsored Attacks
Related: Google Warns G Suite Customers of Passwords Stored Unhashed Since 2005
Related: Hackers Bypass MFA on Cloud Accounts via IMAP Protocol
Related: Google Helps G Suite Admins Enforce Strong Passwords











