With the month not quite complete, Fortinet, in an effort to get the results out before the distractions of a holiday weekend in the U.S., today revealed its Threat Landscape report for June 2010.

The month of June showed new variations of the Sasfis botnet entering the Top malware 10 list along with the re-emergence of older threats. Sasfis, which has been competing with the Pushdo botnet in terms of sheer volume, was very active this month.
“We observed Sasfis loading a spambot component, which was heavily used to send out binary copies of itself in an aggressive seeding campaign,” said Derek Manky, project manager, cyber security and threat research, Fortinet. “The Sasfis socially-engineered emails typically had two themes; one looked like a fake UPS Invoice attachment, and the other was disguised as a fees statement. Much like the Pushdo and Bredolab botnets, Sasfis is a loader – the spambot agent is just one of multiple components downloaded.”
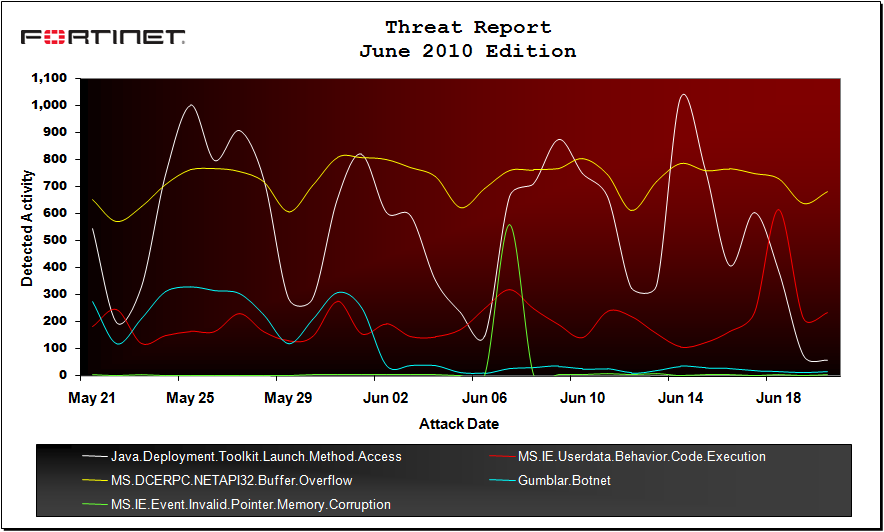
In June, Fortinet discovered the re-emergence of a hit-and-run attack with an Internet Explorer HTML Object Memory Corruption Vulnerability (known as CVE-2010-0249 at Microsoft and MS.IE.Event.Invalid.Pointer.Memory.Corruption at Fortinet). This attack first surfaced in January 2010 and used in the infamous Aurora attacks to plant spy trojans within targeted, major corporations. The attack has since subsided, last appearing in FortiGuard’s top 10 in February’s Threat Landscape report.
Additional threat activities for the month of June include:
• 200 New Vulnerabilities: FortiGuard Labs covered more than 200 new vulnerabilities this period, nearly double from last report.
• Flash and Excel Vulnerabilities: Four Flash and Excel vulnerabilities were disclosed and patched this period.
• Malicious Javascript Code: In terms of malware, the only detection that topped the aforementioned botnet binaries was JS/Redir.BK – obfuscated JavaScript code, which had a surge of activity on June 12 and June 13. The JavaScript code redirected users to various legitimate domains hosting an injected HTML page named “z.htm.”
Top 10 Attacks for June 2010
| Rank | Vulnerability | Percentage | Severity | Shift |
| 1 | Java.Deployment.Toolkit.Launch.Method.Access | 60.2 | Critical | – |
| 2 | MS.IE.Userdata.Behavior.Code.Execution | 17.2 | Critical | – |
| 3 | MS.DCERPC.NETAPI32.Buffer.Overflow | 12.8 | Critical | – |
| 4 | Gumblar.Botnet | 6.7 | Critical | – |
| 5 | MS.IE.Event.Invalid.Pointer.Memory.Corruption | 5.1 | Critical | +13 |
| 6 | Apache.Expect.Header.XSS | 4.2 | Medium | +1 |
| 7 | FTP.USER.Command.Overflow | 3.7 | High | +1 |
| 8 | AWStats.Rawlog.Plugin.Logfile.Parameter.Input.Validation | 3.4 | High | -2 |
| 9 | SMTP.Auth.Buffer.Overflow | 3.3 | Critical | – |
| 10 | MS.IE.Deleted.DOM.Object.Access.Memory.Corruption | 3.3 | Critical | +4 |
FortiGuard observed JavaScript code was circulated through an HTML attachment in spam emails using various themes. In one attack, the HTML containing the malicious JavaScript code was attached as the file “open.htm” in an e-mail urging the user to update their MS Outlook client. The exact same e-mail also circulated with a FakeAV binary attachment, once again proving that spam templates are often recycled for various attacks. In another example, a “bad news” email socially engineered for the FIFA World Cup, had the same malicious JavaScript attached through a file named “news.html.”
“There is no doubt that JavaScript is one of the most popular languages used today for attacks,” Manky continued. “It is used in a growing number of poisoned document attacks (PDF), particularly with heap-spray based techniques. It’s also used to launch exploits, and it is popular as a browser redirector to malicious sites, since the JavaScript code can be obfuscated and appear to be more complex than traditional IFrame based attacks from the past.”
Fortinet’s monthly threat report is compiled from threat statistics and trends for June based on data collected from the company’s FortiGate network security appliances and intelligence systems in located around the world.
















