A critical vulnerability in Apple’s FaceTime chat application can be exploited to spy on people. The tech giant has disabled a FaceTime feature in an effort to prevent abuse until a patch is made available.
Videos and descriptions of the vulnerability have been making the rounds on social media websites. The attack does not require any technical knowledge and it can be carried out in seconds.
The attacker calls the targeted user via FaceTime and then immediately initiates a group chat by using the “Add person” button from the bottom of the screen. The attacker adds their own number to the group chat and FaceTime treats this action as if the targeted user answered the call, thus allowing the attacker to hear the victim.
On the victim’s side, it appears that they haven’t answered the call and there is no indication that the person on the other end can hear them.
Even more worrying, as The Verge and others have discovered, if the victim presses their device’s power button during the incoming call, the attacker also sees them through their camera. At this point, the victim can also hear the attacker, but the screen still shows the incoming call. Some have reported that there are also other ways to get access to video using this flaw.
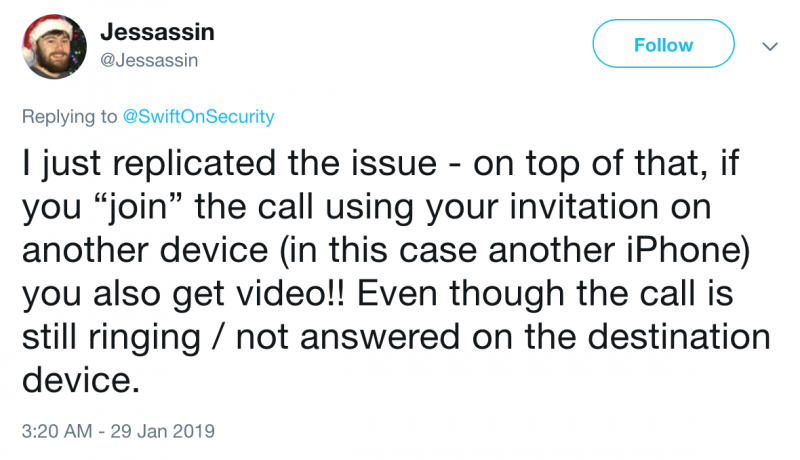
The bug reportedly affects FaceTime on the latest versions of iOS and macOS. Apple says it’s working on a fix and in the meantime it has suspended the Group FaceTime feature to prevent abuse.
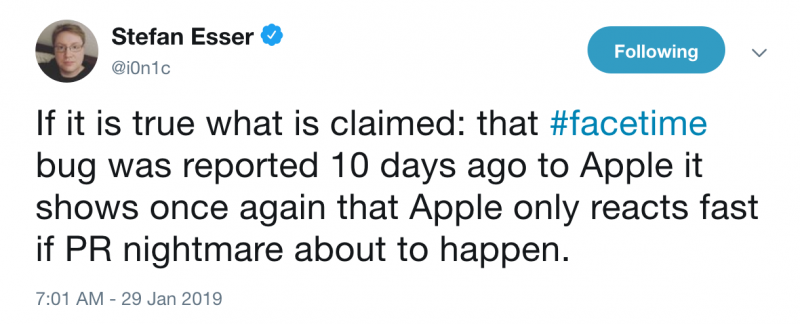
While the origin of the flaw has not been confirmed, one US-based individual who uses the online moniker “MGT7” claims her 14-year-old son discovered the issue. She said the bug was reported to Apple more than 10 days ago, but they never heard back from the company.
Google Project Zero researcher Natalie Silvanovich, who in the past discovered several potentially serious FaceTime vulnerabilities, has a theory on the possible cause of the bug.

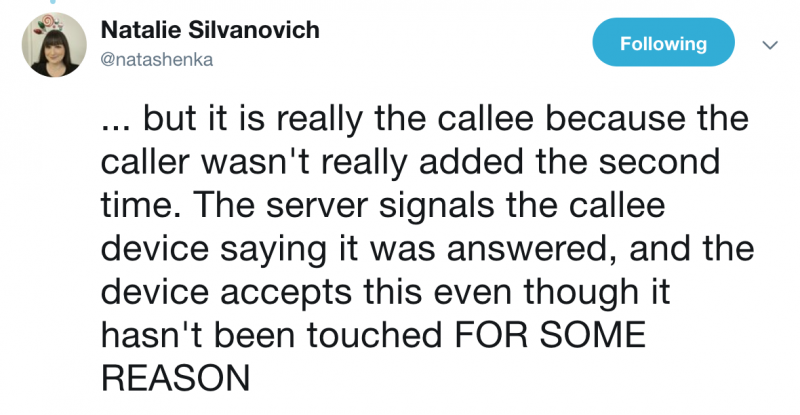
Industry professionals have commented on the impact of the bug and Apple’s response.
This is not the first time someone has found a way to abuse the recently introduced Group FaceTime feature. A few months ago, an iPhone enthusiast demonstrated that the feature could have been used to bypass a device’s lockscreen and gain access to contact information saved on a device.
*The article has been updated to clarify that MGT7 is the mother of the teen who was allegedly the first to discover the flaw
Related: Apple Patches Dozens of Vulnerabilities in iOS, macOS
Related: Apple Patches Passcode Bypass, FaceTime Flaws in iOS
Related: iOS Lockscreen Bypass Abuses New Group FaceTime Feature














