New Attacks Targeting Tibetan and Uyghur Activists Found Using Android Trojan
Targeted attacks against Tibetan and Uyghur activists are nothing new, but attackers appear to be expanding their arsenal of attack tools to the Android platform.
While attacks against the activists in the past have targeted both Windows and Mac OS X-based platforms, researchers from Kaspersky Lab have discovered an APT that successfully leverages Android to compromise targets.
According to Kaspersky researchers, a high profile Tibetan activist had his email account hacked on March 24th, 2013.
Attackers then used the hacked account to send spear phishing emails to the victim’s contact list that included a malicious Android Package (APK) attachment named “WUC’s Conference.apk”.
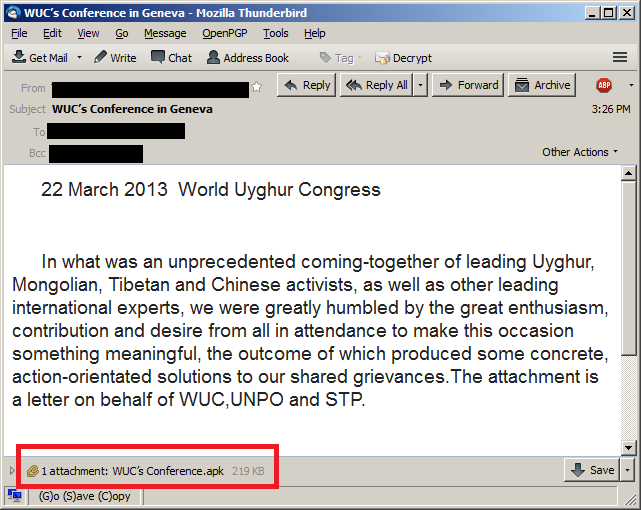
As seen above, the theme of the attack email was a human rights conference event in Geneva, something Kaspersky says has been used in previous attacks targeting Windows users.
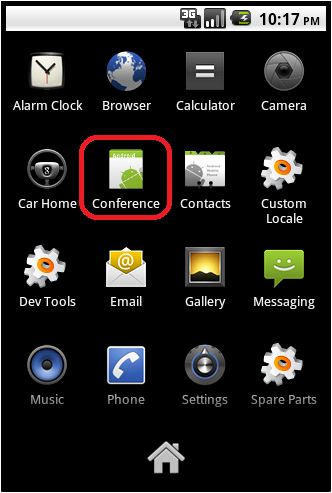
Once the Android package is successfully installed, an application called ‘Conference’ shows up on the Android desktop as depicted in the screenshot to the right.
If the victim launches the malicious app, text about the upcoming event is displayed, appearing to be written by “Dolkun lsa Chairman of the Executive Committee Word Uyghur Congress”. Note that the attackers incorrectly used “Word” instead of “World” in the text.
As the victim reads the fake message, the malware silently contacts a C&C server located in Los Angeles, California and then starts to harvest data stored on the device.
The stolen data includes contacts, call logs. SMS messages, geolocation and other phone data such as phone number, OS version, phone model, and SDK version, Kaspersky said.
Oddly, the researchers found that the stolen data isn’t sent to the C&C server automatically by the malware, but instead waits for incoming SMS messages that contain one of the following commands: “sms”, “contact”, “location”, “other”. If any of these commands is found, the malware proceeds to encode the stolen data with Base64 and sends it off to the command and control server.
Throughout the code, Kaspersky said, attackers log important actions, likely for debugging purposes, indicating the malware may be an early prototype version.
Kaspersky researchers also discovered a domain that points to the same C&C server IP address: “DlmDocumentsExchange(dot)com”, which was was registered on March 8th, 2013 to “peng jia”, using the email address bdoufwke123010(at)gmail.com.
Also of interest, is that researchers found that the C&C server is hosting an index page that serves up an APK file named “Document.apk”, which has the same functionality as the one Conference.apk but uses text in Chinese, about relations between China, Japan and the disputed “Senkaku Islands / Diaoyudao Islands / Diaoyutai Islands”.
The command and control server is running Windows Server 2003 and is configured using the Chinese language, indicating that the attackers are likely Chinese speaking.
“Every day, there are hundreds if not thousands of targeted attacks against Tibetan and Uyghur supporters,” the researchers noted. “The vast majority of these target Windows machines through Word documents exploiting known vulnerabilities such as CVE20120158, CVE20103333 and CVE20093129.”
“Until now, we haven’t seen targeted attacks against mobile phones, although we’ve seen indications that these were in development,” the blog post explained.
“[The attack] is perhaps the first in a new wave of targeted attacks aimed at Android users,” the post continued. “So far, the attackers relied entirely on social engineering to infect the targets. History has shown us that, in time, these attacks will use zero-day vulnerabilities, exploits or a combination of techniques.”
Kaspersky detects the Android malware used in the attack as “Backdoor.AndroidOS.Chuli.a” with an MD5 of 0b8806b38b52bebfe39ff585639e2ea2.
Additional technical details on the malware and the attacks can be found here.
















