Video conferencing giant Zoom on Thursday unveiled an open source vulnerability impact scoring system that it has been developing for the past year.
The Vulnerability Impact Scoring System, or VISS, is a customizable framework that provides a web-based user interface and algorithms to help organizations assess and prioritize vulnerabilities based on actual demonstrated exploitation rather than theoretical impact.
The company says VISS aims to complement the widely used Common Vulnerability Scoring System (CVSS), helping enhance incident response capabilities.
Zoom has been testing the system within its bug bounty program since March and said the use of VISS has led to an increase in reports describing critical and high-severity vulnerabilities, with researchers investing more time and energy to demonstrate the practicality of their exploits.
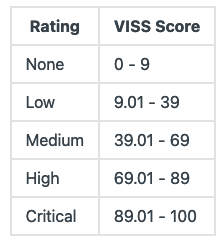
VISS analyzes vulnerabilities based on 13 impact aspects focusing on platform, infrastructure and data. The severity of impact is shown by a numerical score ranging from 0 to 100, which is also influenced by a ‘compensating controls’ metric, which enables the user to specify the existence of compensating security controls that would mitigate exploitation.
It remains to be seen how widely VISS gets adopted by organizations. The fact that it has been developed by a commercial organization could lower its chances of being widely used.
There are several other vulnerability scoring and classification systems, including Stakeholder-Specific Vulnerability Categorization (SSVC), Exploit Prediction Scoring System (EPSS), and Tenable’s Vulnerability Priority Rating (VPR).
While they are being used to some extent, they seem unlikely to replace or be widely used alongside CVSS, which has been the industry standard for many years.
CVSS has some issues, including subjectivity, narrow scope, and improper representation of real-world risks. However, the recently launched CVSS 4.0 aims to address some of these limitations.
On the other hand, the general consensus seems to be that CVSS should not be used on its own to score risk or prioritize vulnerability patching.
Related: Traffic Light Protocol 2.0 Brings Wording Improvements, Label Changes
Related: Zoom Paid Out $3.9 Million in Bug Bounties in 2022
Related: FDA Approves Use of New Tool for Medical Device Vulnerability Scoring