Researchers have identified more than a dozen vulnerabilities in the NicheStack TCP/IP stack, which appears to be used by many operational technology (OT) vendors. The vulnerabilities are collectively tracked as INFRA:HALT.
The security holes, discovered by researchers from Forescout Research Labs and JFrog Security Research, can be exploited by an attacker for remote code execution, denial-of-service (DoS) attacks, information leaks, TCP spoofing, and DNS cache poisoning. Of the 14 flaws, two have been rated critical and 10 have been assigned a high severity rating.
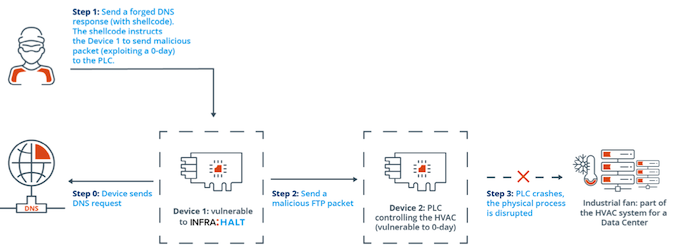
In one theoretical attack scenario described by Forescout and JFrog, an external attacker uses an internet-exposed device running NicheStack to infiltrate the targeted network.
The attacker uses one of the critical INFRA:HALT vulnerabilities that can be exploited by sending specially crafted DNS requests. The malicious DNS request contains shellcode that instructs the first device to send a malicious FTP packet to a second device on the network — a programmable logic controller (PLC) in this example — and cause it to crash. The PLC crash causes the disruption of the physical process associated with the controller.
A search conducted using the Shodan search engine showed more than 6,400 internet-connected devices running NicheStack, including more than 4,000 in North America. Forescout’s own Device Cloud knowledge base showed over 2,500 devices from 21 vendors. Many of these devices are industrial control systems (ICS), and the highest number of vulnerable systems were seen in the discrete manufacturing, process manufacturing, and retail sectors.
Daniel dos Santos, research manager at Forescout, told SecurityWeek that the company saw many affected power meters in Device Cloud. He also noted that in addition to the internet-exposed devices affected by the INFRA:HALT flaws, there are also likely many vulnerable systems that are only accessible from the local network.
Learn more about vulnerabilities in industrial systems at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
NicheStack, also known as InterNiche, is a TCP/IP stack that was originally developed by InterNiche Technologies and acquired in 2016 by HCC Embedded. TCP/IP stacks enable vendors to implement basic network communications for IP-connected systems, including IT, OT and IoT devices.
NicheStack has been around for nearly two decades and versions of the product have been distributed by semiconductor vendors such as Altera (Intel), NXP (Freescale), Texas Instruments (Luminary), and STMicroelectronics. NicheStack has also been used as a foundation for other TCP/IP stacks.
A legacy InterNiche website lists roughly 200 companies that — at least at some point — used NicheStack, including major industrial automation companies such as Siemens, Schneider Electric, Rockwell Automation, Honeywell, Emerson and Mitsubishi Electric.
HCC Embedded was informed about the vulnerabilities in September 2020 and it patched them in May 2021 with the release of version 4.3, which is available upon request from the company’s security support team. HCC has advised anyone using NicheStack to review its security advisories and update the vulnerable software in their products.
Some of the impacted vendors have posted links to HCC’s advisories and others will likely post their own advisories in the upcoming period. On the other hand, Forescout and JFrog said many of the vendors they have contacted have yet to share information on whether their products are impacted.
This is not the first time researchers have identified potentially serious vulnerabilities in TCP/IP stacks. Previously discovered issues include AMNESIA:33, NAME:WRECK and NUMBER:JACK.














