The United States is offering big rewards for information on cybercriminals linked to the recently disrupted LockBit ransomware operation, but law enforcement agencies claim to have already identified some individuals.
The UK’s National Crime Agency (NCA) and other law enforcement agencies have seized LockBit domains and servers, causing significant disruption to the cybercrime operation. The seized domains initially only displayed a screen informing visitors of the law enforcement actions, but visitors are now redirected to a site that resembles the known LockBit leak website.
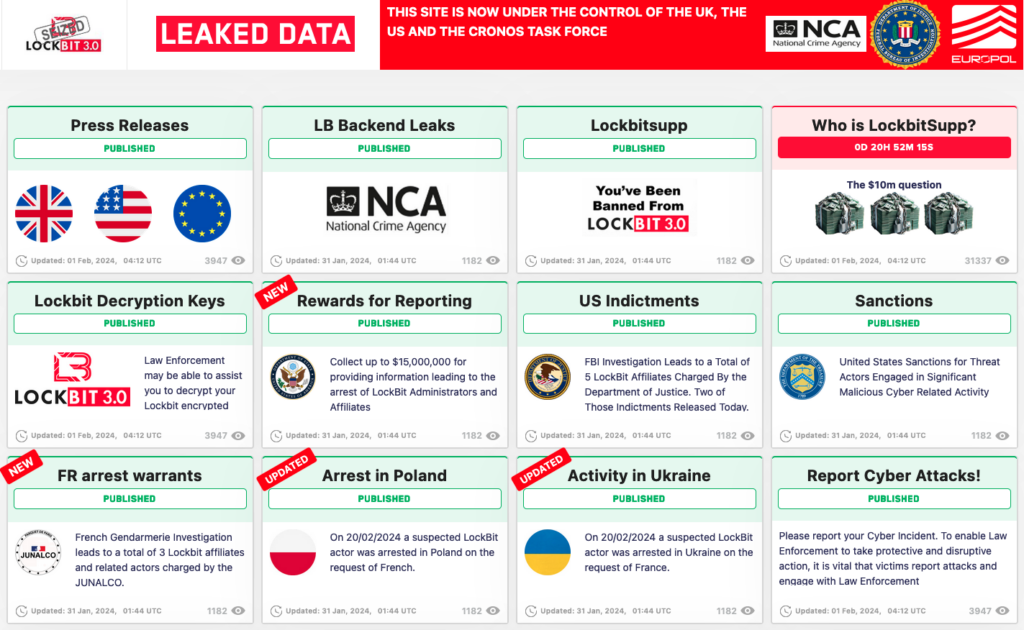
However, instead of the posts announcing LockBit victims, the site displays messages posted by law enforcement, including cybersecurity firm reports on the ransomware group’s activities, information on arrests and charges, rewards for information on the cybercriminals, and sanctions.
The NCA has mocked cybercriminals, posting a message in the hijacked LockBit panel informing affiliates that law enforcement may be in touch with them very soon. On the LockBit leak site, the NCA now displays a list of nearly 200 usernames allegedly associated with LockBit affiliates.
Affiliates receive from the ransomware operators the malware and infrastructure needed to carry out attacks, and they get an agreed-upon percentage of the ransom.
Authorities have also taken down servers associated with a LockBit data exfiltration tool named Stealbit.
“This tool is provided to Lockbit affiliates to facilitate the exfiltration of files from victim organizations and send the files to 1 of 6 upstream proxy servers. The NCA have located these proxy servers and, through the engagement of the FBI and Cronos Group, all 6 have been destroyed. The source code for the script which creates these upstream proxy servers has also been obtained and analyzed. We are also in possession of all variants of the StealBit source code,” the NCA said.
More than 14,000 accounts on services such as Mega, Protonmail and Tutanota, which have been used for infrastructure and data exfiltration, have been shut down.
Investigators also claim to have obtained access to key infrastructure and they may be able to help hundreds of victims recover their files. The NCA said 1,000 decryption keys were recovered and urged victims to get in touch.
Another page on the LockBit leak site suggests that authorities will soon reveal the identity of LockBitSupp, the leader of the ransomware operation.
Law enforcement has also published several screenshots showing privileged access to the LockBit administration portal, including victim chats.
There are also other posts taunting LockBit administrators and affiliates.
The research and threat intelligence project Vx-Underground spoke to LockBit administrators after the law enforcement action came to light. They claimed to be confident that authorities don’t know their real identities and that the wrong individuals have been arrested.
Rewards, charges and sanctions
The Department of State announced rewards totaling up to $15 million for information leading to the arrest and/or conviction of individuals participating in LockBit ransomware attacks. Specifically, up to $10 million is offered for information on LockBit leaders and up to $5 million for information on affiliates.
According to the US government, more than 2,000 entities have been targeted in LockBit ransomware attacks, with victims paying over $120 million in ransoms to the cybercriminals. The losses caused by these attacks are said to total billions of dollars.
The Treasury Department has announced sanctions against two LockBit affiliates. The sanctioned individuals are two Russian nationals: Ivan Gennadievich Kondratiev, aka Bassterlord and Fisheye, alleged leader of a LockBit affiliate sub-group named the National Hazard Society, and Artur Sungatov, an affiliate who has actively engaged in LockBit attacks. The Treasury said Kondratiev had ties to the REvil, RansomEXX and Avaddon ransomware groups as well.
The Justice Department announced charges against Sungatov and Kondratiev this week, bringing the total number of individuals charged over LockBit ransomware attacks to five. One of them is in custody in Canada and is awaiting extradition, and one is in custody in the US and is awaiting trial.
The Treasury’s announcement highlights the LockBit attack on a financial services business of China’s biggest bank, Industrial and Commercial Bank of China (ICBC), which disrupted Treasury market trades.
“The ransomware attack disrupted ICBC’s U.S. broker-dealer, affecting the settlement of over $9 billion worth of assets backed by Treasury securities,” the Treasury said.
Several major ransomware operations have been targeted in international law enforcement operations over the past year, including RagnarLocker, Hive, and BlackCat. However, the impact of such operations could be limited and the cybercriminals may resume their activities under a different name.
In the case of the LockBit takedown, some experts are skeptical about the extent of the impact.
“This disruption will likely be temporary and minimal at best to the organization behind LockBit,” said Jon Marler, cyber evangelist at cybersecurity and compliance company Viking Cloud. “Lockbit’s malware is currently in its third major revision, and without any arrests of the core team that created it, we can only expect more.”
Related: US Offers $10 Million for Information on BlackCat Ransomware Leaders
Related: US Offers $10M Reward for Information on Hive Ransomware Leaders
Related: Ransomware Payments Surpassed $1 Billion in 2023: Analysis


















