The developers of the open source secure messaging app Threema have come under fire over their public response to a security analysis conducted by researchers at the Swiss university ETH Zurich.
The Swiss company that makes Threema claims to have more than 10 million users and over 7,000 on-premises customers. Customers reportedly include the Swiss government and German chancellor Olaf Scholz.
ETH Zurich researchers analyzed the application and its communication protocol last year and discovered seven types of attacks that could be launched by an attacker who can intercept communications, one who has compromised a server, or one who has hacked the targeted user’s device.
According to the researchers, they found issues related to authentication and encryption that could allow an attacker to obtain message metadata (not actual conversations), prevent messages from being delivered, clone accounts, recover the private key associated with a user’s Threema ID, and encrypt potentially compromising messages and deliver them to a user in an effort to plant evidence.
The researchers published a paper detailing their findings and set up a dedicated website for their security analysis of Threema.
The findings were reported to Threema developers in October 2022 and the company has since released mitigations, as well as a new protocol, to mitigate the attack methods.
In a statement published on its website the day the researchers made their findings public, Threema thanked them, but noted that none of the attack methods they described “ever had any considerable real-world impact”.
The company pointed out that the attacks are not easy to pull off, requiring extended physical access to an unlocked device, extensive social engineering, or considerable computing resources.
“Most [attacks] assume extensive and unrealistic prerequisites that would have far greater consequences than the respective finding itself,” Threema said in a blog post.
The statement downplays the findings, but that is not uncommon for vendors. However, a message posted by Threema on Twitter led to the company being vastly criticized by the cybersecurity community.
“There’s a new paper on Threema’s old communication protocol. Apparently, today’s academia forces researchers and even students to hopelessly oversell their findings,” the company wrote in a message pointing to its official statement.
The company’s blog post on the matter was initially titled “New Paper on Old Threema Protocol”, but was later renamed to “Statement on ETH Findings”.
Kenneth Paterson, an ETH Zurich professor involved in the research, described the tweet as “unexpectedly dismissive”, claiming that the Threema protocol was updated thanks to their work.
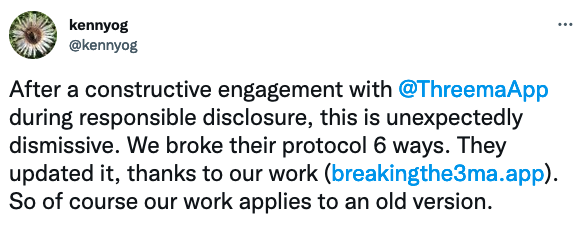
Threema, on the other hand, denies this and claims that the introduction of the new protocol “was planned for some time and coincided with the disclosure period of the researchers”.
Members of the cybersecurity community described the company’s response as aggressive, unprofessional, and arrogant. It seems that the vulnerabilities gained more attention due to Threema’s poor response rather than the actual severity of the flaws.
Related: Google Rolls out E2EE For Android Messages App
Related: Encrypted Services Providers Concerned About EU Proposal for Encryption Backdoors
Related: Swiss Army Knifes WhatsApp at Work













