A threat actor — likely a state-sponsored cyberespionage group — has used a sophisticated technique to allow a piece of malware hosted on a server to communicate with command and control (C2) servers through a firewall.
The attack was spotted by Sophos, which has named the method used by the hackers “Cloud Snooper.” The company came across the attack while investigating a malware infection on an AWS-hosted server, but says the attack may work against any server that is behind a firewall, including on-premises servers.
In the attack analyzed by Sophos, the compromised systems were running both Windows and Linux EC2 instances. While the AWS security groups were configured to only allow inbound HTTP or HTTPS traffic to reach the server, a hacked Linux system was also accepting connections on TCP ports 2080 and 2053, which the attackers opened.
It’s unclear exactly how the attackers planted the malware, but researchers believe they may have accessed the server through a dictionary attack on an exposed SSH port.
The hackers deployed a rootkit that in turn installed a backdoor Trojan. The backdoor, which the attackers could have used to steal sensitive data from the targeted entity, communicated with the C&C server through the rootkit.
Researchers identified backdoors on one Windows system and multiple Linux hosts. An analysis showed that the Windows backdoor was based on the Gh0stRAT malware.
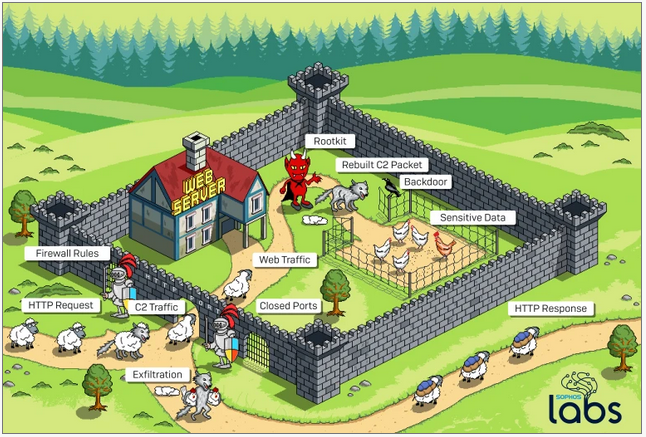
In order to bypass the server’s firewall, the attackers disguised C2 traffic as legitimate traffic. This ensures that the firewall does not block traffic that contains instructions for the malware or traffic that contains data sent back to the C2 server.
“In order to get around the firewall rules, the attackers communicate with the rootkit by sending innocent-looking requests to the web server on the normal web server ports. A listener that inspects inbound traffic before it reaches the web server intercepts the specially-crafted requests, and sends instructions to the malware based on characteristics of those requests,” explained Sergei Shevchenko, threat research manager at Sophos.
“The listener sends a ‘reconstructed’ C2 command to the backdoor Trojan installed by the rootkit. Depending on the commands included into C2 traffic, the attacker may use the backdoor to steal sensitive data from the target,” Shevchenko added. “The collected data is then delivered back with the C2 traffic. Only this time, the rootkit has to masquerade it again in order to bypass the [firewall] once again. Once outside, the C2 traffic delivers the collected data back to the attackers.”
While the individual techniques observed in this attack are not new, Sophos says this is the first time they have been combined in this manner.
“The complexity of the attack and the use of a bespoke APT (Advanced Persistent Threat) toolset gives us reason to believe that the malware and its operators were an advanced threat actor, possibly nation-state sponsored,” Shevchenko said.
Related: New Windows Process Injection Can Be Useful for Stealthy Malware
Related: BlackBerry Cylance Downplays, Patches Antivirus Bypass
Related: Flaw Allowed Attackers to Bypass FireEye Detection Engine
Related: Malware Detection Bypass Vulnerability Found in Cisco Firepower














