Splunk, the maker of software that helps organizations gather and make use of machine data from a diverse set of sources, today released the latest version of the Splunk App for Enterprise Security.
The Splunk App for Enterprise Security, now in version 2.4, combined with Splunk Enterprise, creates a security intelligence platform that helps organizations find unknown threats in real time, such as detecting a malicious payload on a host system and its outbound communication, the company said.
 “Statistical analysis is the new weapon of the security warrior defending against threats that bypass traditional security detection systems,” said Mark Seward, senior director of security and compliance, Splunk. “Companies now understand that hidden in the terabytes of user-generated machine data are abnormal patterns of activity that represent the presence of malware or the behavior of malicious insiders.”
“Statistical analysis is the new weapon of the security warrior defending against threats that bypass traditional security detection systems,” said Mark Seward, senior director of security and compliance, Splunk. “Companies now understand that hidden in the terabytes of user-generated machine data are abnormal patterns of activity that represent the presence of malware or the behavior of malicious insiders.”
The new version of the Splunk App for Enterprise Security enables statistical analysis of HTTP traffic to help security professionals determine a baseline for what’s normal, and detect outliers and use those events as starting points for security analysis and investigation, Seward said.
(Screenshot of Main Dashboard of Splunk App for Enterprise Security)
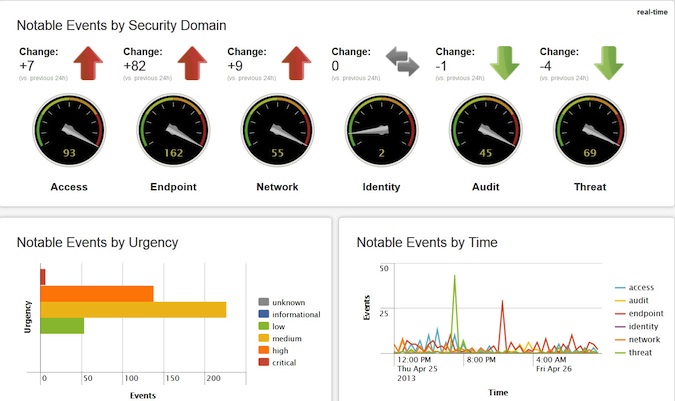
Through statistical analysis, the Splunk App for Enterprise Security reveals attacks and threats including:
• Command and control (CNC) instructions embedded in URLs. The Splunk App for Enterprise Security automates the process to watch for outliers in the data.
• Hosts communicating with new malicious websites. Hosts that are talking to domains registered in the past 24-48 hours indicate a likely CNC site. Splunk users can correlate domain registrations and proxy data to monitor this in real time and historically.
• Significant increases in unknown communications. Monitoring proxy data for specific users with the Splunk App for Enterprise Security enables organizations to watch for spikes of unknown communications as an overall trend and by specific users.
• Unusual user agent strings in use. User agents automate the collection of data such as email, but during attacks user agents strings can also facilitate automated victim attacker communications. Splunk customers can monitor and be alerted about user agent anomalies in real time.
• Abnormal amounts of source/destination traffic. Track average amounts of traffic are tracked between source/destination pairs and calculated over user specified time frames. Statistical outliers are visualized in a scatter plot and can be used to start an investigation.
“The future of securing the enterprise relies upon using all available data, not just predetermined bits and pieces of traditional security data. Statistical analysis expands the value of that data. It can help uncover meaningful insight that often goes unrecognized in a mass of raw information,” said Scott Crawford, managing research director, security and risk management, Enterprise Management Associates.
Existing Splunk customers who have purchased the Splunk App for Enterprise Security can download version 2.4 of the Splunk App for Enterprise Security on Splunkbase, the company said.













