Hackers Leak Athlete Medical Data From Olympics Anti-Doping Agency
The World Anti-Doping Agency (WADA) has officially pointed the finger at a Russian cyberespionage group for breaching its systems and leaking sensitive athlete data, including confidential medical records, but a hacktivist group has also taken credit for the attack.
WADA hacked via password phishing
WADA, a non-profit organization founded by the International Olympic Committee (IOC) and supported by national governments, informed stakeholders last month that malicious actors had registered two fake WADA domains which they had leveraged to phish credentials for the Anti-Doping Administration and Management System (ADAMS). Yuliya Stepanova, a whistleblower who exposed widespread doping in Russian athletics, was one of the victims of the attack.
Researchers quickly found connections between the attack on WADA and the notorious Russia-linked threat actor known as Fancy Bear, APT28, Pawn Storm, Strontium, Sofacy, Tsar Team and Sednit.
On Tuesday, WADA published a statement confirming that a Russian spy group was behind the attack on its systems. The organization doesn’t appear to have reached this conclusion on its own – it got the information from law enforcement authorities.
WADA said the hackers used phished credentials to access athlete data, including test results from the Rio Games and Therapeutic Use Exemptions, some of which they published online.
“WADA condemns these ongoing cyber-attacks that are being carried out in an attempt to undermine WADA and the global anti-doping system,” said Olivier Niggli, director general of WADA. “Let it be known that these criminal acts are greatly compromising the effort by the global anti-doping community to re-establish trust in Russia further to the outcomes of the Agency’s independent McLaren Investigation Report.”
Russian espionage or hacktivism?
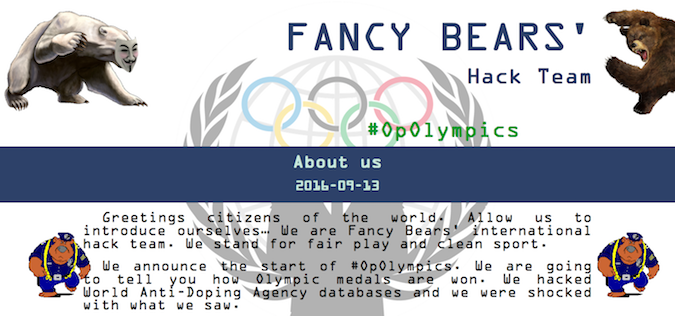
The group that leaked the athlete data is calling itself “Fancy Bears’ international hacking team” and its website, fancybear.net, suggests that it’s affiliated with the Anonymous hacktivist movement.
The hackers claim they have launched OpOlympics, a campaign whose goal is to show that famous athletes from the U.S. and other countries won medals at the Olympics by using substances banned by WADA. The group even accepts Bitcoin donations on its website.
The group has so far leaked test results and other medical documents on American athletes, including gymnast Simone Biles, basketball player Elena Delle Donne, and tennis players Venus and Serena Williams.
“After detailed studying of the hacked WADA databases we figured out that dozens of American athletes had tested positive,” the hackers said. “The Rio Olympic medalists regularly used illicit strong drugs justified by certificates of approval for therapeutic use. In other words they just got their licenses for doping. This is other evidence that WADA and IOC’s Medical and Scientific Department are corrupt and deceitful.”
Biles and Donne reacted to the data leak on Twitter, claiming they had been taking the WADA-banned substances for genuine medical conditions. The U.S. Anti-Doping Agency (USADA) also published a statement backing the claims of the affected athletes.
“The athletes haven’t [done anything wrong],” said USADA CEO Travis T. Tygart. “In fact, in each of the situations, the athlete has done everything right in adhering to the global rules for obtaining permission to use a needed medication. The respective International Federations, through the proper process, granted the permission and it was recognized by the IOC and USADA.”
Russia has denied any involvement in the attack on WADA. However, it’s worth noting that this is not the first time the country has been accused of a cyberattack for which “hacktivists” take credit.
When the U.S. Democratic Party’s systems were breached this summer, experts immediately pointed the finger at the APT28/Fancy Bear threat group, but a hacktivist using the online moniker “Guccifer 2.0” took credit for the attack. Now, evidence again seems to point at Russia and a hacktivist group calling itself “Fancy Bears’ Hacking Team” takes credit.
In the case of Guccifer 2.0, who has claimed to be Romanian, although he has failed to prove it, some researchers believe he is actually a personna used by cyberspies to throw investigators off track.
Related: More Evidence Links Russia to DNC Attack
Related: Evidence Links Russia to Second Democratic Party Hack
















